Firefox for Pentester: Privacy and Protection Configurations
Introduction
This is a second article in the series “Firefox for Pentester”. Previously we talked about how we can enhance the Privacy and Protection in Firefox using various add-ons and so, in this article we will become competent to protect ourselves online through the configuration options that Firefox provides us. In comparison to other browsers, Firefox protects our data and information the most. And we all know that Mozilla Firefox is plausibly the best browser available today. It provides privacy features, active development, amazing security, and the cherry on top is it has frequent updates. But we can still make it much more secure by modifying a few options.
Table of Content:
- Introduction
- Configuration Settings
- Isolating First Party Domains
- Preventing Browser Fingerprinting
- Enabling Tracking Protection (Browser Fingerprinting)
- Enabling Tracking Protection (Crypto Mining)
- Enabling Tracking Protection
- Blocking Ping Tracking
- Disabling URL Preloading
- Keeping Clipboard Private
- Disabling EME Media
- Restricting DRM Content
- Disabling Media Navigation
- Restricting Cookie Behaviour
- Control Referrer Header
- Restricting Referrer Header
- Restricting WebGL
- Disabling Session Restoring
- Disabling Beacon
- Securing Remote Downloads
- Firefox Prefetching
- Disabling IDN Punycode Conversion
- Conclusion
Configuration Settings
When playing with the configurations in Firefox, numerous elements should be examined. Every option should be understood well enough for the changes to be made as they will change the way you browse your internet. To make changes in configurations of Firefox, type “about:config” in the URL bar as shown in the image below:

Once the about:config page loads, it will show you a warning. The warning will state that from here on if you change anything then it will void your warranty and whatever changes you make will be at your own risk. To move forward from here left click on the “I accept the risk!” as shown in the image above. Once you click on the button, you will meet with the page shown in the image below. Here are all the options regarding online privacy and protection present.

Isolating first-party Domains
Through the first option, we will modify is “privacy.firstparty.isolate”. This built-in characteristic allows you to only access first-party domains. That means all the third-party domains that tag along the first-party domains are now blocked and cannot track your activity online or collect your data. All this is possible as it isolates the first-party domains from others and stores your data separately so that cross-origin tracking is nullified. Hence, third-party cookies, hidden cookies, data sharing, and other options will be disabled.
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
privacy.firstpart.isolate

Preventing browser fingerprinting
The next option is “privacy.resistFingerprinting”. To understand what this option does, let us first understand what is browser fingerprinting. Client-side scripting that allows the website to load in the browser permits browser fingerprinting. Through this, they collect the information about the browser, operating system, cache-control header, all kinds of headers, list of fonts, plugins that are being used, microphone, camera, etc. Hence, they are called cookie-less monsters. This process of browser foot-printing starts the moment a connection is made with the website. And these features are exploited through credential hijacking, data breaching, etc. All of this can be stopped by enabling the “privacy.resistFingerprinting” option in your browser.
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
privacy.resistFingerprinting

Enabling Tracking Protection (Browser Fingerprinting)
The next option that we are going to talk about is privacy.trackingprotection.fingerprinting.enabled . It works the same as the previous one. As this one too protects you from browser fingerprinting. Along with preventing tracking over the websites, it also prevents phishing attacks.
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
privacy.trackingprotection.fingerprinting.enabled

Enabling Tracking Protection (Crypto Mining)
The problem with crypto miners is that the calculations they do, require huge resources such as CPU, power, and RAM. These resources are expensive and not everyone can afford it. So, what hackers do is that they control systems of various people and carry out the deed of crypto mining from there system. So to stop your browser to fall victim to cryptomining all you have to do it enable the privacy.trackingprotection.cryptomining.enabled option.
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
privacy.trackingprotection.cryptomining.enabled
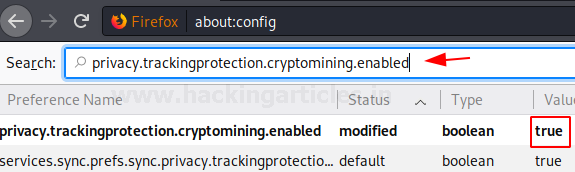
Enabling Tracking Protection
Our next option i.e. privacy.trackingprotection.enabled enables us to completely stay non-existent to the tracking that is done through the browser. Tracking is keeping a record of your internet searches, the website you visit, data you share, etc. and this option nullifies it by blocking every kind of tracking. It works on the disconnect.me filter list.
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
privacy.trackingprotection.enabled
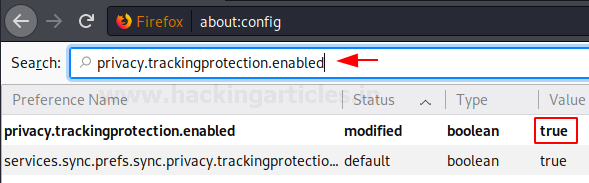
Blocking Ping tracking
To understand the next option which is the browser.send_pings, let us first understand hyperlink auditing. It is a method of tracking where the HTML code makes your browser ping a specified URL. This URL is pinged upon the visitation of the website that you mean to visit. This method is of tracking is different from other methods as it doesn’t give users any kind of choice. It just runs in the background without the user knowing. So to shut this method of tracking, you have to go into the configuration of the Firefox and disable the browser.send_ping option. This option here makes sure that the browser blocks every kind of hyperlink auditing.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default as to allow hyperlink auditing. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
browser.send_pings
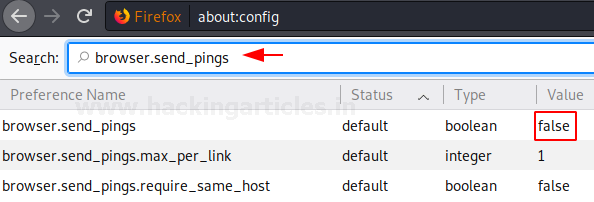
Disabling URL preloading
This browser.urlbar.speculativeConnect.enabled option helps us to control URL preloading. Whenever typing in the URL, halfway through the typing you must have noticed the auto-completion of the URL. This is known as URL preloading. How this works is when you start by typing a URL, it will send out domain queries so that it can carry on with auto-completion. And so, by disabling it, the preloading of URLs into the URL bar will stop. This helps to prevent the suggestions which you do not want or which can be presumed as insecure.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
browser.urlbar.speculativeConnect.enabled
Keeping Clipboard Private
Whenever you copy, cut or paste anything from or to the website; it gets notified in detail so much as that they will know what part of the webpage you copied. This is done by keeping a track of your clipboard. Through the dom.event.clipboardevents.enabled option we can make sure that the websites do not track our data from the clipboard.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
dom.event.clipboardevents.enabled

Disabling EME Media
There have been many instances recorded where medias files have been downloaded. These files were proved to be encrypted when they downloaded their self, it was hard to detect them and their data. Firefox provides us with an option through which we can make sure nothing of such sorts happen.
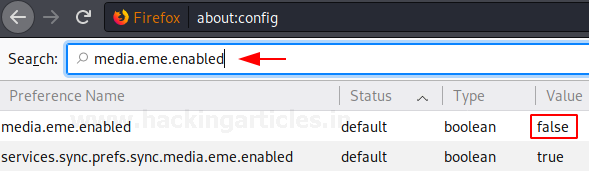
This media.eme.enabled option is set to false by default. This means that no encrypted media will be download without the user’s permission. It can be searched through the search bar. If by any chance this option is enabled, make sure to disable it as soon as possible. And if it is disabled by default then the status of this configuration will remain default as shown in the image below:
media.eme.enabled
Restricting DRM Content
The content you surf on the internet can never be trusted. Usually, when DRM based software’s are running on the website, they can have file-level control and even user-level control. The user-level control allows them to access, share, download, or print anything they desire. Therefore, you must be in control always. Even if your browser nags you to enable DRM content you shouldn’t fall for it because if you do not want to see it shouldn’t be able to see it. Firefox provides us with an option i.e. media.gmp-widevinecdm.enabled that allows you to restrict DRM content.
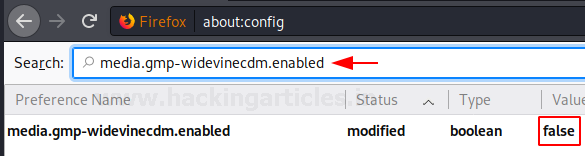
This option can be searched through the search bar. By default, this option is set to the value false i.e. it is disabled by default as messes up the authentication system of many websites. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to true. Setting the value from false to true will mean that you have now enabled this option. Once the option is enabled, the status of the option will be changed from default to modified as shown in the image below:
media.gmp-widevinecdm.enabled
Disabling Media Navigation
This option, if enabled will allow your browser to extract information from your system and present it to the websites you visit. The data collected from the system can be forwarded to the Third-party domains as well. The thing is if you allow this option then it will collect the information about the operating system, screen resolution, type of system, FrameRate, facingMode of the mobile devices, possible access to user media, etc. And to make it even worse, they can control permissions of the audio/visual tabs in the browser as well as access the camera or microphone. Hence, we all can come to an agreement that keeping this option enabled is a major threat. And to save us from the potential threats, we just have to disable the media.gmp-widevinecdm.enabled option.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
media.navigator.enabled

Restricting Cookie Behaviour
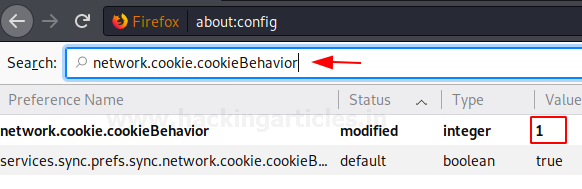
There are various cookies generated when a website is visited. These cookies can be necessary which are used for the features of a website. And others are the unimportant cookies such as third-party cookies. These cookies are often the result of advertisements, widgets, and web analytics. They track your login information, shopping carts, language you use, etc. By default, the value for network.cookie.cookiebehaviour is set to 0. This value can be set between the numbers 0 to 4, where:
0 = accept all cookie values
1 = only accept from first-party domains
2 = block all cookies by default
3 = use p3p settings
4 = storage access policy: Block cookies from trackers
We will select value 1 here as we only want cookies from first-party domains.
network.cookie.cookieBehavior

This option can be searched through the search bar. Once the value of the option is changed, the status of the option will be changed from default to modified as shown in the image below:
Control Referrer Header
While browsing the internet, a referrer header is sent to the website which is requested. This header contains the information about the page where u previously was and from where did you request the next webpage. Usually, the Firefox will not send a referrer header from HTTPS to HTTP. Sending such information over a referrer header creates security issues as they can expose your personal information and private data. To put it simply using this option you will be able to control whether you want the referrer to be sent over the cross origins or not. Now, this data can send to different origin domains i.e. across origins. But Firefox’s built-in tracking protection provides a solution to it through network.http.referer.XOriginPolicy option. This value can be set between the numbers 0 to 2, where:
0 = send the referrer in all cases
1 = send referrer only when the base domains are the same
2 = send referrer only on the same origin
The default value of this option is 0 i.e. send the referrer in all cases and we will change its value to 2 i.e. send the referrer only to the same origin.
network.http.referer.XOriginPolicy
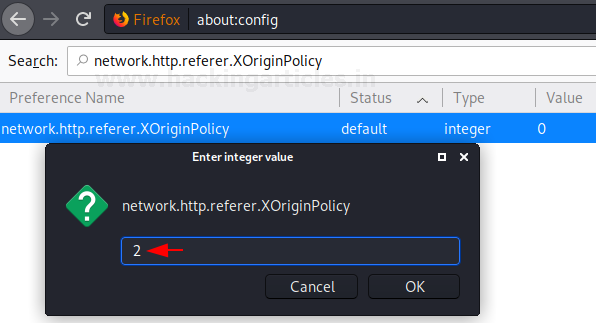
This option can be searched through the search bar. Once the value of the option is changed, the status of the option will be changed from default to modified as shown in the image below:

Restricting Referrer Header
With the previous configuration setting, we learned that we can control whether we want to send referrer headers across origins or not. Now there will be many situations where it will be necessary for you to send these referrer headers across origin or even in the same origin. Here, what you can do it restrict the header by controlling the elements of the header. The option network.http.referer.XOriginTrimmingPolicy allows us to do so. This value can be set between the numbers 0 to 2, where:
0 = send the full URL
1 = send the URL without its query string
2 = only send the origin
The default value of this option is 0 i.e. send the full URL and we will change its value to 2 i.e. only send the origin.
network.http.referer.XOriginTrimmingPolicy
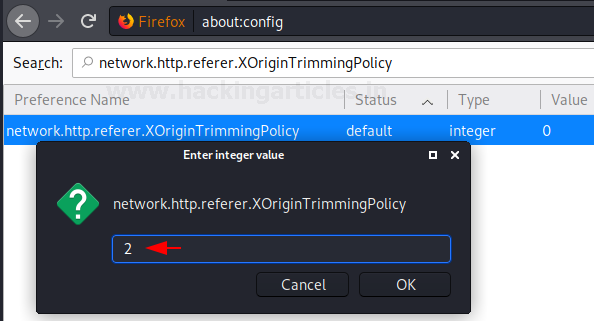
This option can be searched through the search bar. Once the value of the option is changed, the status of the option will be changed from default to modified as shown in the image below:
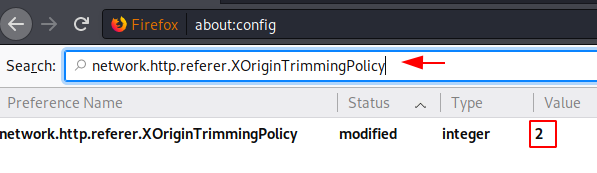
Restricting WebGL
WebGL is an option provided by Firefox which turns every webpage into 3D graphics. Alas! It comes with various security flaws. It makes it possible for the attackers to target your graphic drivers along with GPU to extend of making your whole system useless. Whether you want to use such an option or not is left to user decision by Firefox when it introduced webgl.disable configurational setting. Through this option, you can disable the WebGL.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. But if you are pro-privacy and anti-tracking like us then you should double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
webgl.disabled

Disabling Session Restoring
There are times where the user experiences some crashes or power outages that cause the system to shut down. If the user has some URLs opened in the browser or logged in some application they are restored when the user restarts the system. Ever since the release of Firefox 2.0 this option is enabled by default. Some users feel that this is a good functionality that helps them recover data or sessions but this poses a security threat as the if the original intended user doesn’t restart the system or if this happens on a Public system than the person who accesses the system after the restart gains the potential access of that logged-in sessions and websites that the original user was browsing. This option contains 3 possible values.
0 = Store Extras Session data for any site
1 = Store Extra Session data for unencrypted (non-HTTPS) sites only
2 = Never store extra session data
The default value of this option is 0 i.e. Store the session data for any site and we will change its value to 2 i.e. Never store any data.
browser.sessionstore.privacy_level
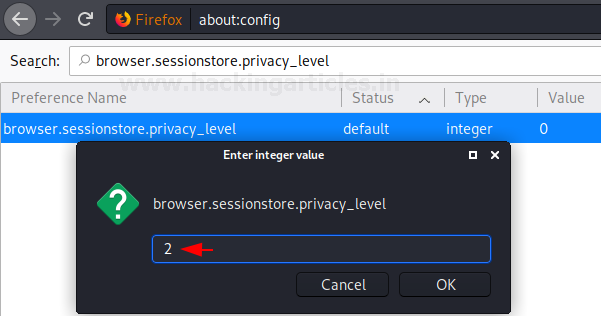
This option can be searched through the search bar. Once the value of the option is changed, the status of the option will be changed from default to modified as shown in the image below:

Disabling Beacon
IEEE 802.12.4 says that beacon-enabled mode is to be applied through the network. It sends information about the personal network to the servers to inform them about the presence. This allows new devices to connect from time to time. It is useful to maintain network synchronization. But it not compulsory as it sends over the details about the network you are on.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. You can double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
beacon.enabled

Securing Remote Downloads
By default, remote safe downloads are enabled in Firefox. And we have often talked about the instances where the file that is being downloaded seems genuine but instead, it can be a malware. And you can never be too sure. Using browser.safebrowsing.downloads.remote.enabled we can be a step closer to know we are downloading safe files and nothing is remotely tagging along with the file.
This option can be searched through the search bar. By default, this option is set to the value true i.e. it is enabled by default. You can double left-click on this option to change its value to false. Setting the value from true to false will mean that you have now disabled this option. Once the option is disabled, the status of the option will be changed from default to modified as shown in the image below:
browser.safebrowsing.downloads.remote.enabled

Firefox Prefetching
As the name tells, prefetching in Firefox is done to speedily load webpages for the user. A browser can always summon the parameters beforehand that it knows will be used by the websites. These parameters contain data regarding resources to be used. Hence, at any point in time, they can be request and the browser will prefetch the required information for the user. The browser will foretell the domain names that you are most likely to visit which speeds up the process of domain name resolving. This option was developed to save time on the user end but it turned out to be a security concern. Firefox can prefetch things like DNS, network, IP address, etc.
This prefetching can be done via DNS (everything related to DNS) or HTTPS (HTTPS contents). And has been proved to be a security concern and so both DNS and HTTPs prefetching can be disabled via the following options:
network.dns.disablePrefetch
network.dns.disablePrefetchFromHTTPS
Both options are set to false by default. To disable these options, change them to true and there will be no DNS and HTTPS prefetching. Once these options are disabled, the status of these options will be changed to locked just as it is shown in the image below:

Another prefetcher that you can disable is network predictor. This option prefetch all the details related to the network that you are connected to. It can be disabled by setting it value to false. This value is set to be true by default. Once the change option’s value to false; its status is changed to modified as shown in the image below:
network.predictor.enabled

Another option to disable to disallow the browser to prefetch network details is network.predictor.enable-prefetch. This option is allowing all the network details to be prefetched as its name suggests. It can be disabled by setting it value to false.
network.predictor.enable-prefetch

The network.prefetch-next option allows certain links to be prefetched. This is done when the website lets the browser know that certain pages are likely to be visited. Therefore, the browser downloads them beforehand for the convenience of the users. It can be disabled by setting it value to false. This value is set to be true by default. Once the change option’s value to false; its status is changed to modified as shown in the image below:
network.prefetch-next
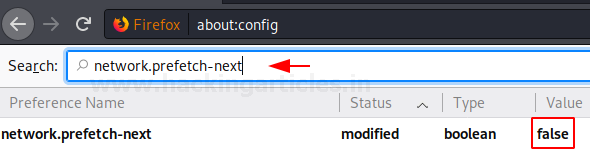
Disabling IDN Punycode Conversion
Before understanding this particular option, first, you need to understand the meaning of IDN support. IDN makes it possible for the website to register the domain names using the characters that are originated from their local or native language. To expand the support of these characters a new encoding was developed called “Punycode”. By default, the value network.IDN_show_punycode is false. This means IDN is enabled. But no matter how good a feature is, it can be abused. This was shown when in 2005 there was a huge rise in Spoofing and Phishing attacks using IDNs. This can be explained using the following example:
Original Domain: https://hackingarticles.in
Pishing Domain: https://hackingarticlés.in
Notice the é in the pishing domain. When this option is enabled it converts é to e so that users that don’t use é in their language can see it as simple e. But this conversion also makes it impossible for a user to visually differentiate between the genuine and phishing domains.
This value is set to be false by default. Once the change option’s value to true; its status is changed to modified as shown in the image below:
network.IDN_show_punycode

Conclusion
By enabling and disabling the configurations options provided by Firefox you can achieve privacy and protection online without using plug-ins. This is a safe procedure as the third-party domain cannot track you. If you are having issues with any particular web application or authentication or media with these options enabled/disabled then what you should do is create a container in Firefox by using a temporary container plugin or profiling that is provided by Firefox. So that you are safe and cross-origin tracking isn’t done in your browser. Hence your data and personal information are safe.
Author: Yashika Dhir is a Cyber Security Researcher, Penetration Tester, Red Teamer, Purple Team enthusiast. Contact her on Linkedin and Twitter