Credential Dumping: Windows Autologon Password
Autologon helps you to conveniently customize the built-in Autologon mechanism for Windows. Rather than waiting for a user to enter their name and password, Windows will automatically log in to the required user using the credentials you submit with Autologon, which are encrypted in the registry.
In this post, we will try to dump the stored autologin credentials with the help of two different tools.
Let’s see the settings for autologin, first, you need to access the User Accounts Control Panel using netplwiz command inside the run prompt.
Choose the account for autologon, for example, we have selected user Raj.

Enter your password once and then a second time to confirm it and uncheck the box “Users must enter a user name and password to use this computer” then click OK.

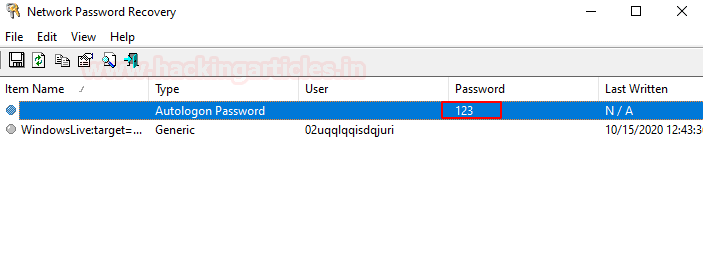
Method 1: Nirsoft-Network Password Recovery
Network Password Recovery is very easy to use, install and run the tool on the local machine whose password you chose to extract. It will dump the stored credential for the autologon account.
You can download this tool from here
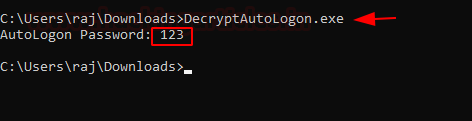
Method 2: DecryptAutologon.exe
This tool can extract/decrypt the password that was stored in the LSA by SysInternals AutoLogo.
You can download its Compiled Version HERE
Run the downloaded .exe as shown in the given image, it will dump the password in the Plain text.
Author: Vishva Vaghela is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here
Hi, I really appreciate and want to thank you for your posts. I really learn a lot about your posts and want to specifically want to ask you to keep posting as I learn a lot about them. As a Director and Founder of my Company a Cyber and Digital Forensics Company in my country South Africa, I says THANK YOU