Understanding Nmap Scan with Wireshark
In this article, you will learn how to capture network packet using Wireshark when an attacker is scanning target using NMAP port scanning method. Here you will notice that how Wireshark captured different network traffic packet for open and close ports.
Note: The Below Practical is performed with the same IP address (192.168.1.102), which you will notice is common for our Windows and Linux Machine, you may differentiate them by their MAC addresses in this case.
Let’s start!!!
TCP Scan
Tcp scan will scan for TCP port like port 22, 21, 23, 445 etc and ensure for listening port (open) through 3-way handshake connection between the source and destination port. If the port is open then source made request with SYN packet, a response destination sent SYN, ACK packet and then source sent ACK packets, at last source again sent RST, ACK packets.
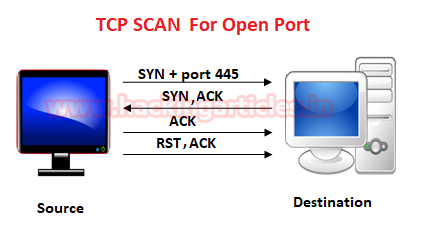
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
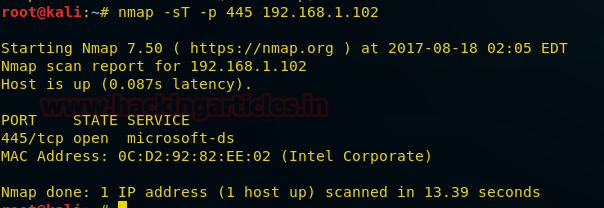
nmap -sT -p 445 192.168.1.102
From the given image you can observe the result that port 445 is open.
Look over the sequence of packet transfer between source and destination captured through Wireshark.
You will notice that it has captured the same sequence of the flag as described above:
- Source sent SYN packet to the destination
- Destination sent SYN, ACK to source
- Source sent ACK packet to the destination
- Source again sent RST, ACK to destination

Let’s figure out network traffic for the close port. According to a given image, it is showing if scanning port is closed then 3-way handshake connection would be not possible between source and destination.
Source sent SYN pack and if the port is close the receiver will be sent a response through RST, ACK.
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sT -p 3389 192.168.1.102
From the given image you can observe the result that port 3389 is closed.

Look over the sequence of packet transfer between source and destination captured through Wireshark.
You will notice that it has captured the same sequence of the flag as described above:
- Source sent SYN packet to the destination
- Destination sent RST, ACK packet to the source

Stealth Scan
SYN scan is the default and most popular scan option for good reasons. It can be performed quickly, scanning thousands of ports per second on a fast network not hampered by restrictive firewalls. It is also relatively typical and stealthy since it never completes TCP connections.
The port is also considered open if an SYN packet (without the ACK flag) is received in response.
This technique is often referred to as half-open scanning because you don’t open a full TCP connection. You send an SYN packet as if you are going to open a real connection and then wait for a response. An SYN, ACK indicates the port is listening (open)

Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
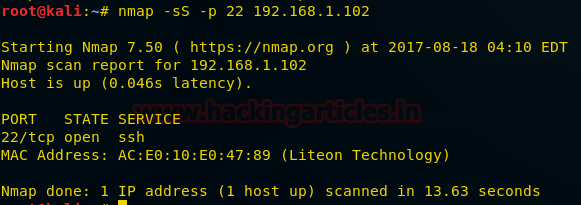
nmap -sS -p 22 192.168.1.102
From the given image you can observe the result that port 22 is open.
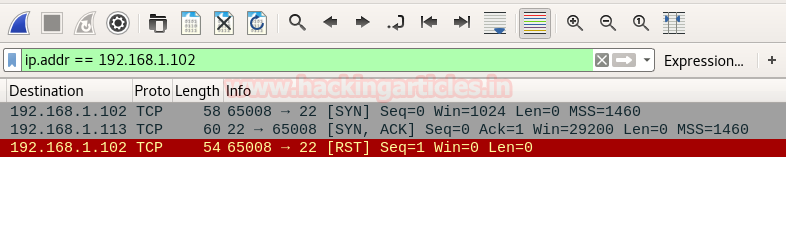
Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent SYN packets to the destination
- Destination sent SYN, ACK packets to the source
- Source sent RST packets to the destination
Now figure out traffic for close port using stealth scan. When source sent SYN packet on the specific port then if the port is closed then the destination will reply by sending RST packet.

Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sS -p 3389 192.168.1.102
From the given image you can observe the result that port 3389 is closed.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent SYN packets to the destination
- Destination sent RST, ACK packets to the destination

Fin Scan
A FIN packet is used to terminate the TCP connection between the source and destination port typically after the data transfer is complete. In the place of an SYN packet, Nmap starts a FIN scan by using a FIN packet. If the port is open then no response will come from destination port when FIN packet is sent through source port.
Fin-Scan are only workable in Linux machines and does not work on the latest version of windows

Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sF -p 22 192.168.1.102
From the given image you can observe the result that port 22 is open.
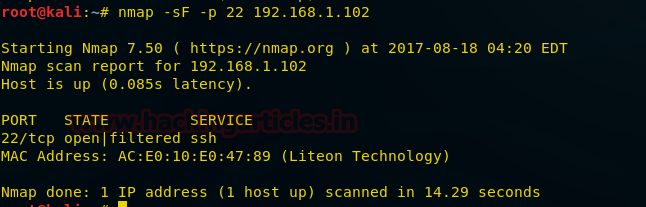
Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent FIN packets to the destination
- Destination sent no reply to the source
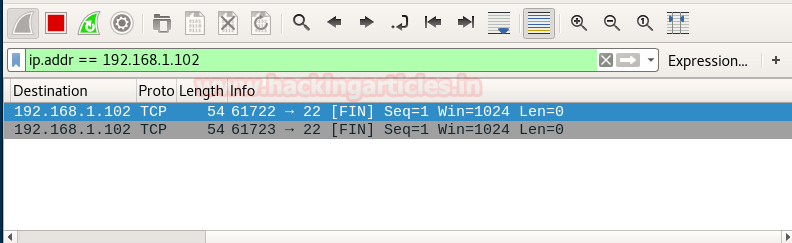
Similarly, if Fin scan is performed against any close then source port will be sent FIN packet to specific port and destination will reply by sending RST, ACK packets.

Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sF -p 3389 192.168.1.102
From the given image you can observe the result that port 3389 is closed.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent SYN packets to the destination
- Destination sent RST packets to the destination

Null Scan
A Null Scan is a series of TCP packets which hold a sequence number of “zeros” (0000000) and since there are none flags set, the destination will not know how to reply the request. It will discard the packet and no reply will be sent, which indicate that the port is open.
Null Scan is only workable in Linux machines and does not work on latest version of windows
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sN -p 22 192.168.1.102
From the given image you can observe the result that port 22 is open.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent Null packets to the destination
- Destination sent no reply to the source
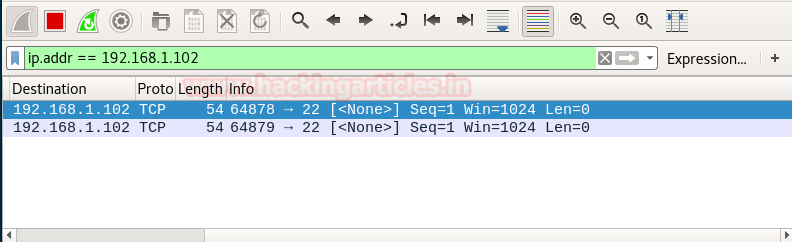
If the port is closed, the Destination will send an RST, ACK packet in response when source send null packets on a specific port

Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sN -p 3389 192.168.1.102
From the given image you can observe the result that port 3389 is closed.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent Null (none) packets to the destination
- Destination sent RST, ACK to source
UDP Scan
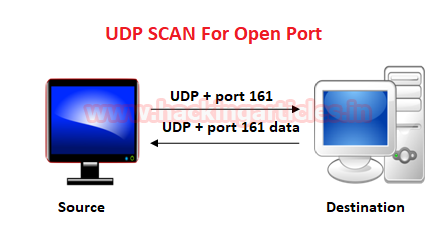
UDP scan works by sending a UDP packet to every destination port; it is a connectionless protocol. For some common ports such as 53 and 161, a protocol-specific payload is sent to increase the response rate, a service will respond with a UDP packet, proving that it is open. If no response is received after retransmissions, the port is classified as open|filtered. This means that the port could be open, or perhaps packet filters are blocking the communication.
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sU -p 161 192.168.1.119
From the given image you can observe the result that port 161 is open.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent UDP packets to the destination
- Destination sent UDP packet with some data to the source

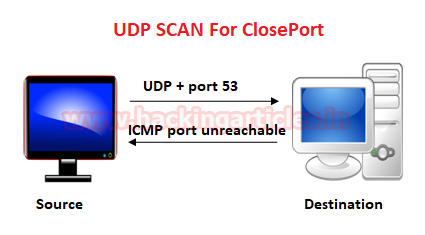
Similarly, if source sent UDP packet on a close port to the destination then destination sent a reply with ICMP packet port unreachable with an appropriate error.
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
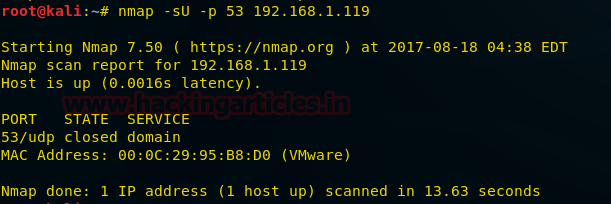
nmap -sU -p 53 192.168.1.119
From the given image you can observe the result that port 53 is closed.
Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent UDP packets to the destination
- Destination sent ICMP packet port unreachable to the source

Xmas Scan
These scans are designed to manipulate the PSH, URG and FIN flags of the TCP header, Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree. When source sent FIN, PUSH, and URG packet to a specific port and if the port is open then destination will discard the packets and will not send any reply to the source.
Xmas Scan is only workable in Linux machines and does not work on the latest version of windows
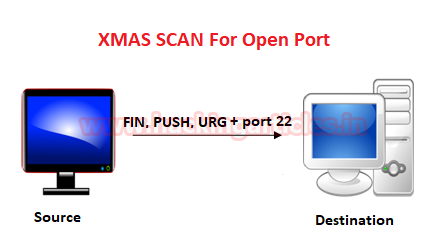
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
nmap -sX -p 22 192.168.1.102
From the given image you can observe the result that port 22 is open.

Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent FIN, PUSH and URG packets to the destination
- Destination sent no reply to the source

Similarly, if source sent FIN, PUSH and URG packets to a specific port and if the port is closed then destination will be sent RST, ACK packets to the source.
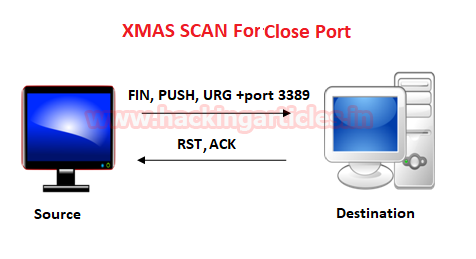
Type following NMAP command for TCP scan as well as start Wireshark on another hand to capture the sent Packet.
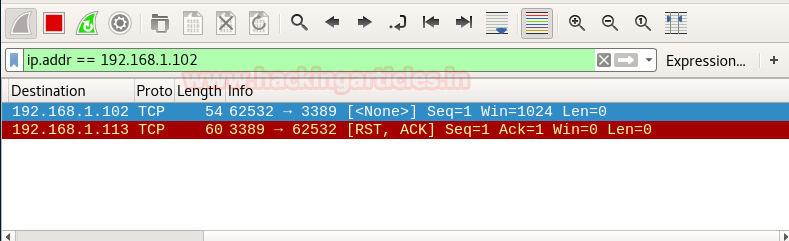
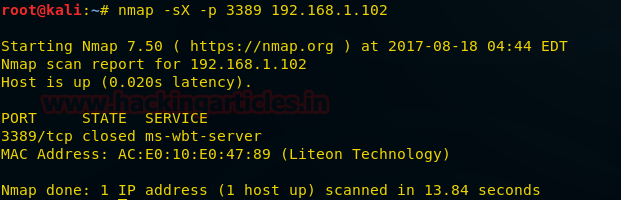
nmap -sX -p 3389 192.168.1.102
From the given image you can observe the result that port 3389 is closed.
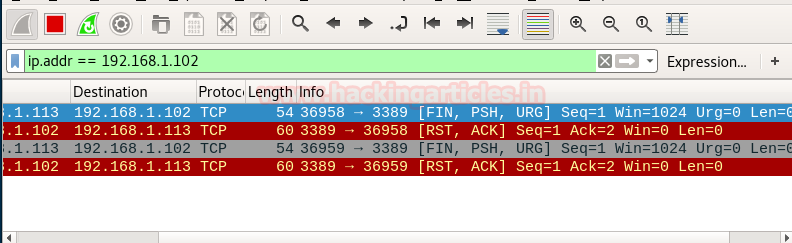
Look over the sequence of packet transfer between source and destination captured through Wireshark
- Source sent FIN, PUSH and URG packets to the destination
- Destination RST, ACK packet to the source
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here

Amazing article. Thanks for sharing this stepwise guideline to tackle the attacker invasion using wireshark. Great explanations and easy to understand. Thanks a million for sharing this.
A good article!
Man, this is just great! Thank for sharing
can you also show how to detect nmap -O (OS) using wirehsark
Good Artical Raj.. Appreciate your efforts on sharing good Artical.