Nmap Scans using Hex Value of Flags
In this article, we are going to scan the target machine by sending TCP flags through their hexadecimal value and the actual Flag name can be confirmed by analysis of Nmap traffic through Wireshark.
Let’s have a look over Hex value of TCP Flag in given below table which we are going to use in Nmap for port enumeration.

NULL Scan
In this scan, we are sending the NONE flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
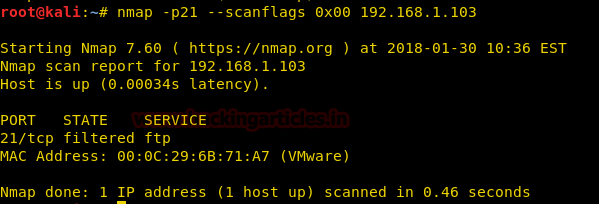
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x00 192.168.1.103
From given below image you can observe we have found port 21 filtered.
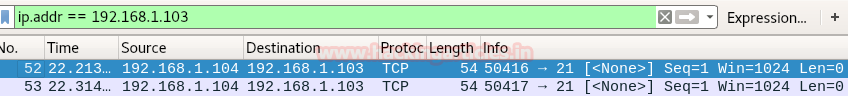
When network admin will capture the incoming traffic he will get a packet for TCP-NONE flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-NONE packet for hex value 0x00 coming from 192.168.1.104 on port 21 as shown in given below image.
FIN Scan
TCP-FIN flag always used for finishing the communication with the target network. In this scan, we are sending the FIN flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x01 192.168.1.103
From given below image you can observe we have found port 21 filtered.

When network admin will capture the incoming traffic he will get a packet for TCP-FIN flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-FIN packet for hex value 0x01 coming from 192.168.1.104 on port 21 as shown in given below image.

SYN Scan
TCP-SYN flag always initiates communication to establish a connection with the target network. In this scan, we are sending the SYN flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
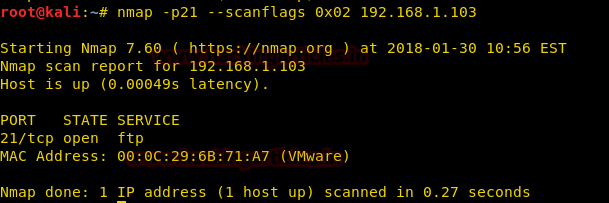
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x02 192.168.1.103
From given below image you can observe we have successfully found port 21 open.
When network admin will capture the incoming traffic he will get a packet for TCP-SYN flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-SYN packet for hex value 0x02 coming from 192.168.1.104 on port 21 as shown in given below image.

Reset Scan
RST flag is used to reset the connection between the sender machine and the target machine. In this scan, we are sending the RST flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
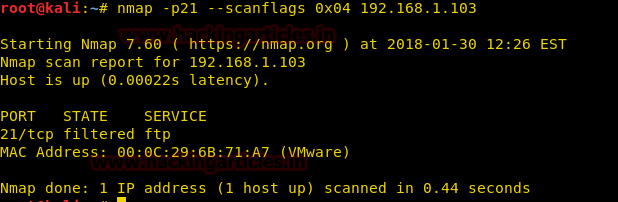
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x04 192.168.1.103
From given below image you can observe we have found port 21 filtered.
When network admin will capture the incoming traffic he will get a packet for TCP-RST flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-RST packet for hex value 0x04 coming from 192.168.1.104 on port 21 as shown in given below image.

PUSH Scan
In this scan, we are sending the PSH flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x08 192.168.1.103
From given below image you can observe we have found port 21 filtered.

When network admin will capture the incoming traffic he will get a packet for TCP-PSH flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-PSH packet for hex value 0x08 coming from 192.168.1.104 on port 21 as shown in given below image.
PUSH flag is used to push the process priority higher of the packet to the target machine.

ACK Scan
Ack flag is used to acknowledge the sender machine whether the packet is received or dropped by the target. So that the sender again sends the lost or dropped packet on the target network to complete the communication process. Here we are sending the ACK flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x10 192.168.1.103
From given below image you can observe we have found port 21 closed.
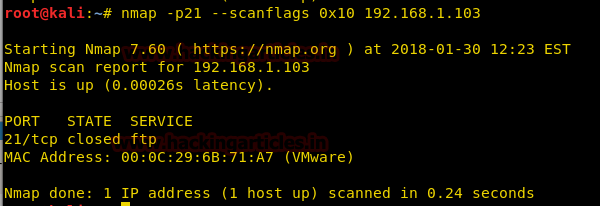
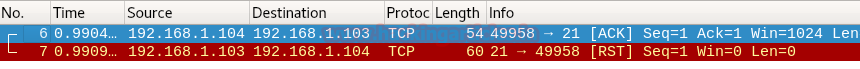
When network admin will capture the incoming traffic he will get a packet for TCP-ACK flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-ACK packet for hex value 0x10 coming from 192.168.1.104 on port 21 as shown in given below image.
Open and closed ports will both return an RST packet. Nmap then labels them as unfiltered, meaning that they are reachable by the ACK packet, but whether they are open or closed is undetermined. Ports that don’t respond, or send certain ICMP error messages back (type 3, code 0, 1, 2, 3, 9, 10, or 13), are labeled filtered. (From Nmap.org)
Urgent Scan
URG flag is used to set the high process priority of the packet to the target. So that target machine stops processing the current packet and process the URG Flag packet. In this scan, we are sending the Urg flag of the tcp by using its hexadecimal value on the target machine to enumerate the state of ports is open, closed or filtered.
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x20 192.168.1.103
From given below image you can observe we have found port 21 filtered.

When network admin will capture the incoming traffic he will get a packet for TCP-URG flag, here we have used Wireshark for network packet analysis and we found that it is showing TCP-URG packet for hex value 0x20 coming from 192.168.1.104 on port 21 as shown in given below image.

XMAS Scan
In this scan, we are sending the combination of the hexadecimal value of the different flag on the target machine. As we know in Xmas scan combination of three TCP-flags [FIN, PSH, URG] are used to enumerate state of the port.
By adding the value of the flag, which is equal to the hexadecimal value of the sender’s hexadecimal value as described in given below the table.
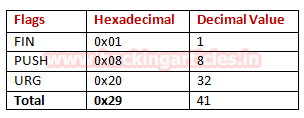
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x29 192.168.1.103
From given below image you can observe we have found port 21 filtered.

When network admin will capture the incoming traffic he will get packet for TCP flags [FIN, PSH, URG] here we have used Wireshark for network packet analysis and we found that it is showing TCP-packet of FIN, PSH, URG for hex value 0x29 coming from 192.168.1.104 on port 21 as shown in given below image.

Manual Combination of Flags [FIN, SYN, PSH]
Let have a quick review over decimal to hexadecimal conversion with the help of the following table:

Now repeat the same methodology by changing the combination of the flag to enumerate the state of any port. For example, we want to scan any port by sending a combination of three flags [FIN, SYN, and PSH] so let identify hex value for the sum of three flags.

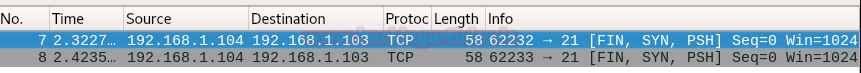
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x0B 192.168.1.103
From given below image you can observe we have found port 21 filtered.

When network admin will capture the incoming traffic he will get packet for TCP flags [FIN, SYN and PSH] here we have used Wireshark for network packet analysis and we found that it is showing TCP-packet of FIN, SYN,PSH for hex value 0x0B coming from 192.168.1.104 on port 21 as shown in given below image.
Manual Combination of Flags [FIN, RST, PSH]
Now repeat the same methodology by changing the combination of the flag to enumerate the state of any port. For example, we want to scan any port by sending a combination of three flags [FIN, RST, and PSH] so let identify hex value for the sum of three flags.

Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x0D 192.168.1.103
From given below image you can observe we have found port 21 filtered.
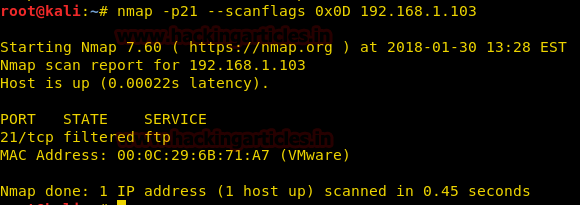
When network admin will capture the incoming traffic he will get packet for TCP flags [FIN, RST, and PSH] here we have used Wireshark for network packet analysis and we found that it is showing TCP-packet of FIN, RST,PSH for hex value 0x0D coming from 192.168.1.104 on port 21 as shown in given below image.

Manual Combination of Flags [FIN, SYN, RST, PSH]
Now repeat the same methodology by changing the combination of the flag to enumerate the state of any port. For example, we want to scan any port by sending a combination of four flags [FIN, SYN, RST, and PSH] so let identify hex value for the sum of four flags.
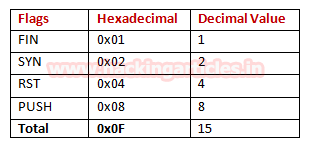
Now execute given below command for enumerating state of any port, here we want to identify state for port 21.
nmap -p21 --scanflags 0x0F 192.168.1.103
From given below image you can observe we have found port 21 filtered.
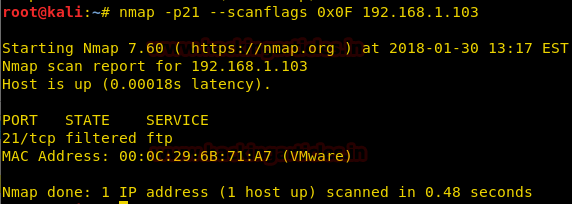
When network admin will capture the incoming traffic he will get packet for TCP flags [FIN, SYN, RST, and PSH] here we have used Wireshark for network packet analysis and we found that it is showing TCP-packet of FIN, SYN, RST, PSH for hex value 0x0F coming from 192.168.1.104 on port 21 as shown in given below image.

Author: Rahul Virmani is a Certified Ethical Hacker and the researcher in the field of network Penetration Testing (CYBERSECURITY). Contact Here