Nmap Scan with Timing Parameters
Hello everyone, in this article we will have a look at the different parameters that are used together to make a timing template and how to use those parameters individually according to will.
Let’s Start!!
Nmap Timing Template
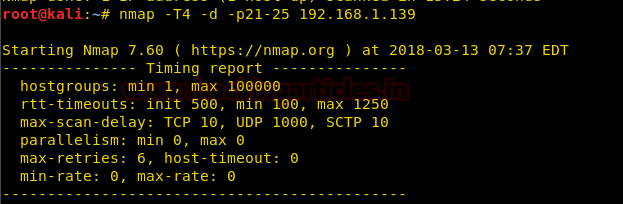
As we have seen that Nmap has multiple timing templates that can be used differently as according to the requirement. Click here to check the timing scan article. Let’s see what’s inside the timing template. to get the description of timing template we’ll use -d attribute.
nmap -T4 –d -p21-25 192.168.1.139
Here we have multiple arguments that collectively make a timing template. Let’s have a look at them one by one.
- Host-groups
- Rtt-timeouts
- Scan-delay
- Max-retires
- Min-rates
- Parallelism
Maximum Retries (–max-retries)
–max-retries specifies the number of times a packet is to be resent on a port to check if it is open or closed. If –max-retries is set to 0, the packets will be sent only once on a port and no retries will be done.
nmap -p21-25 192.168.1.139 --max-retries 0

Here in Wireshark, we can see that 1-1 TCP SYN packet sent to each port from source: 192.168.1.126 to destination: 192.168.1.139 are not sent again.

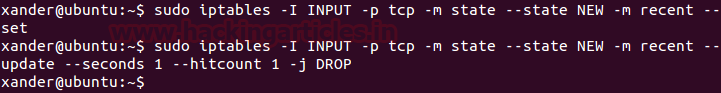
Now we will apply a small firewall rule on the target machine so that the packets get blocked if they come at a faster rate.
sudo iptables -I INPUT -p tcp -m state --state NEW -m recent --set sudo iptables -I INPUT -p tcp -m state --state NEW -m recent --update --seconds 1 --hitcount 1 -j DROP
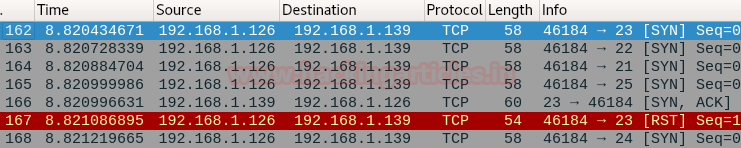
Now, the normal scan will not show any results with max-retries
nmap -p21-25 192.168.1.139 --max-retries 0

As we can see that the ports whose packets got dropped are not sent again so their status is not determined.
here we can increase the max-retries value which will bypass the specified firewall filter so that we can get the exact port status.
nmap -p21-25 192.168.1.139 --max-retries 5
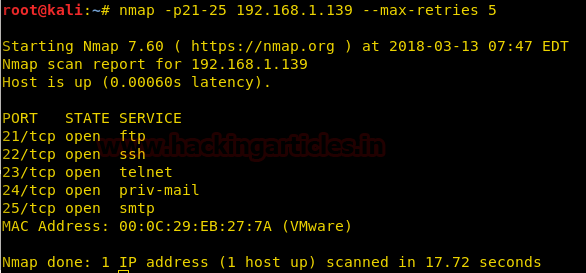
Here we can see that TCP SYN packets sent to one port from source: 192.168.1.126 to destination: 192.168.1.139 are sent again and again until the packets return a specified reply or the maximum retry value (here 5) is reached.
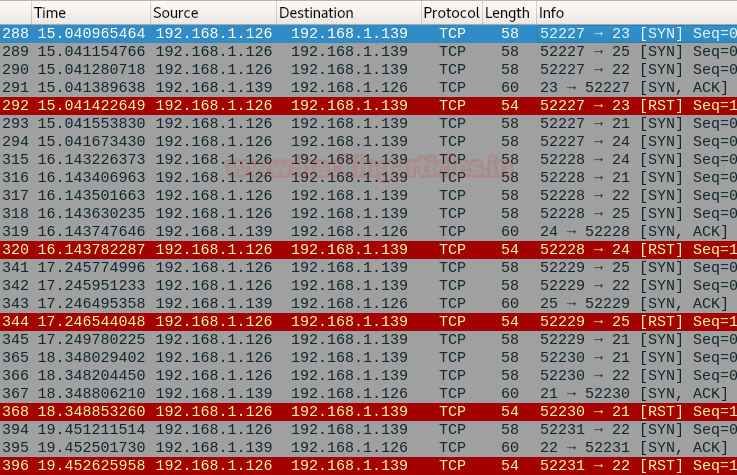
Host-timeout
The –host-timeout is an attribute that specifies the scan to give up on a host after the specified time. The lesser the time specified the more are the chances of inaccuracy in scan results.
We can specify the time in milliseconds (ms), seconds (s), minutes (m)
nmap -p21-25 192.168.1.139 --host-timeout 10ms

Now we will try to get the result by increasing the timeout value
nmap -p21-25 192.168.1.139 --host-timeout 100ms

We can use –host-timeout in other scenarios also like when we need to check if the host system is live or not. Here we have shown how the host-timeout can affect the results of a ping scan.
nmap -sP 192.168.1.139 --host-timeout 10ms
The output from the above command had given 0 hosts is up.
nmap -sP 192.168.1.139 --host-timeout 100ms
The output from the above command had given 1 host is up.

Hostgroup
hostgroup attribute is specified to scan a specified number of hosts in the network at a time. You need to specify the minimum number of hosts or maximum number of hosts or both to be scanned at a time
nmap -sP 192.168.1.1/24 --min-hostgroup 3 --max-hostgroup 3
From given below image you can be observed that it has shown only 3 live hosts from inside complete subnet mask and save your time from scanning the complete network.

Scan delay
Scan delay is used to delay the packet to be sent by the specified time. It is very useful in evading time-based firewalls.
nmap -p21-25 192.168.1.139 --scan-delay 11s
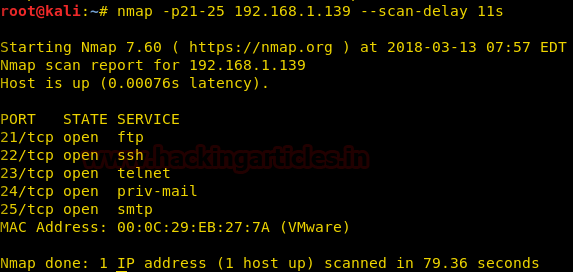
here we can see the time difference in between the packets
packet 1: TCP SYN packet on port 25 at 07:58:01 from 192.168.1.126 to 192.168.1.139

packet 2: TCP SYN packet on port 22 at 07:58:12 from 192.168.1.126 to 192.168.1.139
Now if you will count the time difference between these packets you get 11 sec time laps between these two packets.
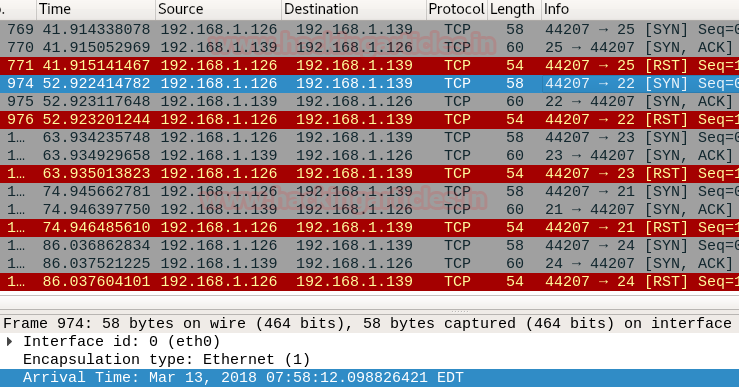
Maximum rate (max-rate)
Rate is an attribute that specifies at what rate is the packets are to be sent, in other words, number of packets to be sent at a time. Max-rate specifies the maximum number of packets to be sent at once.
nmap -p21-25 192.168.1.139 --max-rate 2
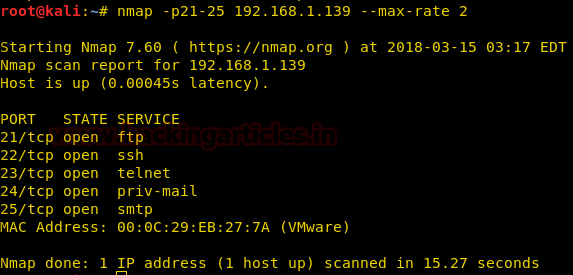
wireshark shows that the packets sending rate are less than 2, means the number of packets sent at a time is less than or equal to 2
packet 1: TCP SYN packet on port 21 at 03:17:20 from 192.168.1.126 to 192.168.1.139
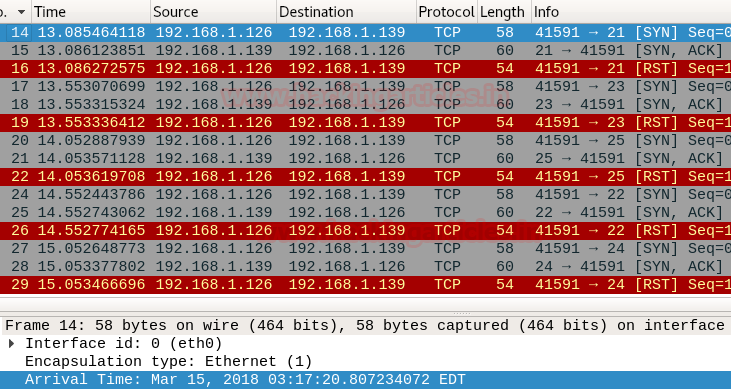
packet 2: TCP SYN packet on port 23 at 03:17:21 from 192.168.1.126 to 192.168.1.139
Now if you will count the time difference between these packets you get 1 sec time laps between these two packets indicating that these two packets were not sent together.

Minimum rate (min-rate)
Min-rate specifies the maximum number of packets to be sent at once. Here if we want at least 2 packets must be sent on target’s network at the same time not less than this, then need to execute below command.
nmap -p21-25 192.168.1.139 --min-rate 2

wireshark shows that the packets sending rate are greater than 2, means the number of packets sent at a time is equal to or greater than 2
packet 1: TCP SYN packet on port 23 at 03:28:29 from 192.168.1.126 to 192.168.1.139
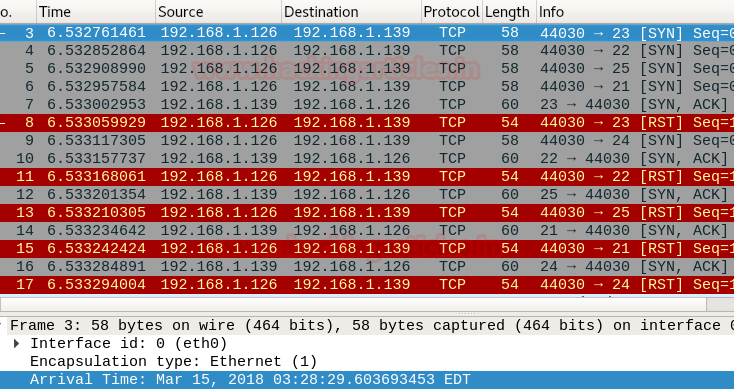
packet 2: TCP SYN packet on port 22 at 03:28:29 from 192.168.1.126 to 192.168.1.139
Now if you will count the time difference between these packets you get only a fraction of second as time laps between these two packets indicating that these two packets were sent together.

Parallelism
Parallelism attribute is used to send multiple packets in parallel, min-parallelism means that the number of packets to be sent in parallel is to be greater than the value specified and max-parallelism means that the number of packets to be sent in parallel is to be less than or equal to the value specified
nmap -p21-25 192.168.1.139 --min-parallelism 2 --max-parallelism 2

In Wireshark we can see a couple of TCP-SYN packets sent in parallel from 192.168.1.126 which is neither less nor greater than 2.

Round trip timeout
Rtt timeout is the time specified for a packet to return a reply, min-rtt-timeout specifies the minimum value of time that is to be taken by a packet to return a reply
nmap -p21-25 192.168.1.139 --min-rtt-timeout 5ms
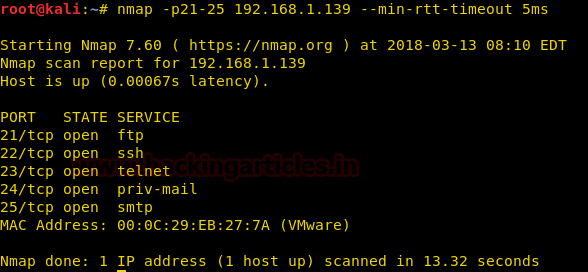
wireshark shows that the packet and its reply takes time greater than the min-rtt-timeout specified
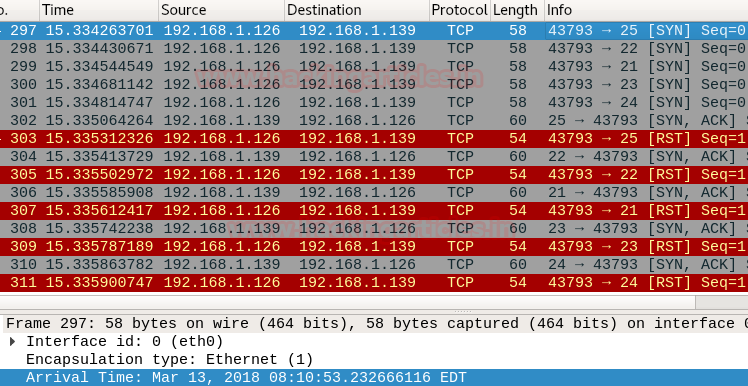
packet 1: TCP SYN packet on port 25 at 08:10:53.232666116 from 192.168.1.126 to 192.168.1.139
packet 2: SYN-ACK packet from port 25 at 08:10:53.233466679 from 192.168.1.139 to 192.168.1.126

Max-rtt-timeout
max-rtt-timeout specifies the maximum value of time that is to be taken by a packet to return a reply
nmap -p21-25 192.168.1.139 --max-rtt-timeout 50ms
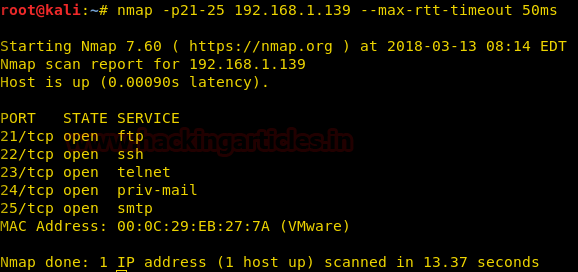
wireshark shows that the packet and its reply takes time lesser than the max-rtt-timeout
packet 1: TCP SYN packet on port 22 at 08:15:08.171777907 from 192.168.1.126 to 192.168.1.139

packet 2: SYN-ACK packet from port 22 at 08:15:08.173117154 from 192.168.1.139 to 192.168.1.126

Initial Round trip timeout
Initial-rtt-timeout specifies the initial value of time to be taken by a packet to return a reply, the return time can be greater or lesser than the initial-rtt-timeout because of the max-rtt-timeout and min-rtt-timeout specifies the range of time for a packet to return a reply but the packet attempts to return a reply in the time specified in initial-rtt-timeout
nmap -p21-25 192.168.1.139 --initial-rtt-timeout 50ms

Wireshark shows that the time taken by the packet to return reply is around the same time as specified in initial-rtt-timeout
packet 1: TCP SYN packet on port 23 at 08:18:45.342395520 from 192.168.1.126 to 192.168.1.139

packet 2: SYN-ACK packet from port 23 at 08:18:45.342930962 from 192.168.1.139 to 192.168.1.126

Author: Deepanshu is a Certified Ethical Hacker and a budding Security researcher. Contact here.