3 ways to scan Eternal Blue Vulnerability in Remote PC
Hello Friends! As we all know that Microsoft Windows 7 are exploitable by eternal blue with SMBv1. Then Microsoft patches this vulnerability by updating the SMB version. Still, there are a large number of Windows 7 users who didn’t update their system. Now if a security tester wants to separate vulnerable system from update system he requires some scanning to identify a vulnerable system.
The eternal scanner is a network scanner for Eternal Blue exploit CVE-2017-0144.
Target: Windows 7
Attacker: Kali Linux
Open the terminal in your Kali Linux and type the following command to download it from GitHub.
git clone https://github.com/peterpt/eternal_scanner.git && cd eternal_scanner

After then when it gets successfully install you need run the script for in the Oder to lunch the scanner on the terminal by typing following:
escan
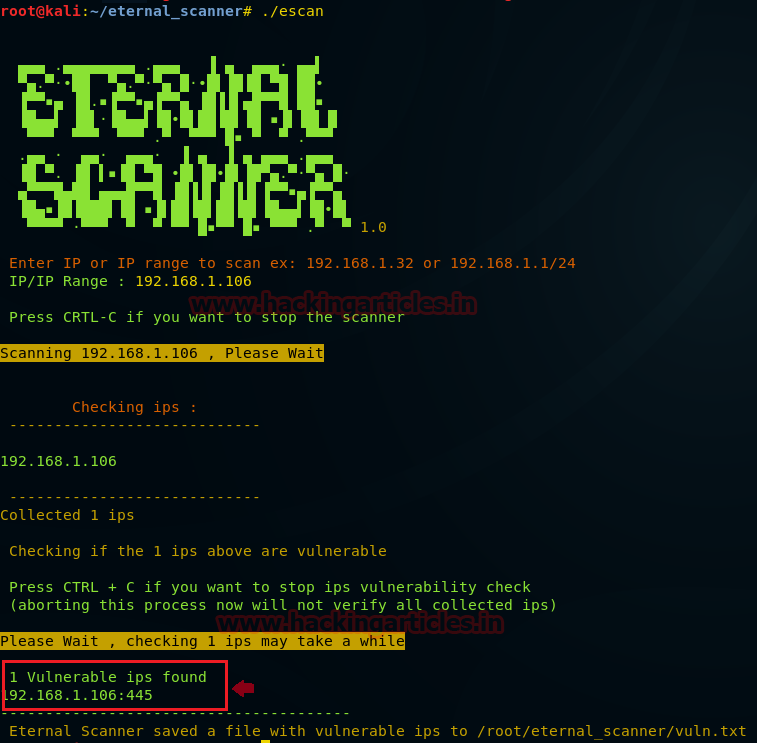
Once the scanner is launched inside the terminal further it will ask to enter target IP or you can also add a range of IPs for scanning.
We have given only single IP for scanning i.e. 192.168.1.106 as a target.
Then it will start scanning and dumb those IP which is vulnerable in given IP range; from the screenshot, you can observe it has dump 192.168.1.106:445 as vulnerable IP with SMB port 445 and save the output inside /root/eternal_scanner/vulnr.txt
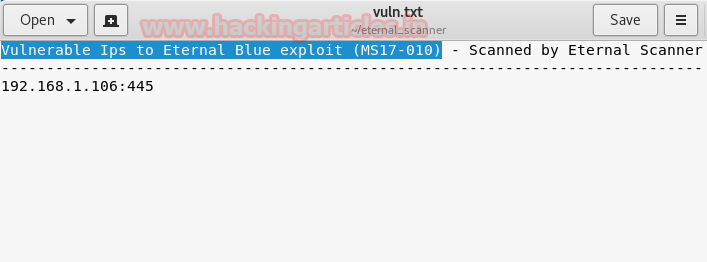
When you will open the output file you will observe vulnerable IP as well as the name of exploit “MS17 -010” as shown in the given image.
Similarly, you can scan the target using NMAP and Metasploit
Nmap
Attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code execution vulnerability (ms17-010, a.k.a. EternalBlue). The vulnerability is actively exploited by WannaCry and Petya ransomware and other malware.
The script connects to the $IPC tree, executes a transaction on FID 0 and checks if the error “STATUS_INSUFF_SERVER_RESOURCES” is returned to determine if the target is not patched against ms17-010. Additionally, it checks for known error codes returned by patched systems.
Tested on Windows XP, 2003, 7, 8, 8.1, 10, 2008, 2012 and 2016.
The following command will scan the SMB vulnerability using in-built certain scripts and report according to the output result.
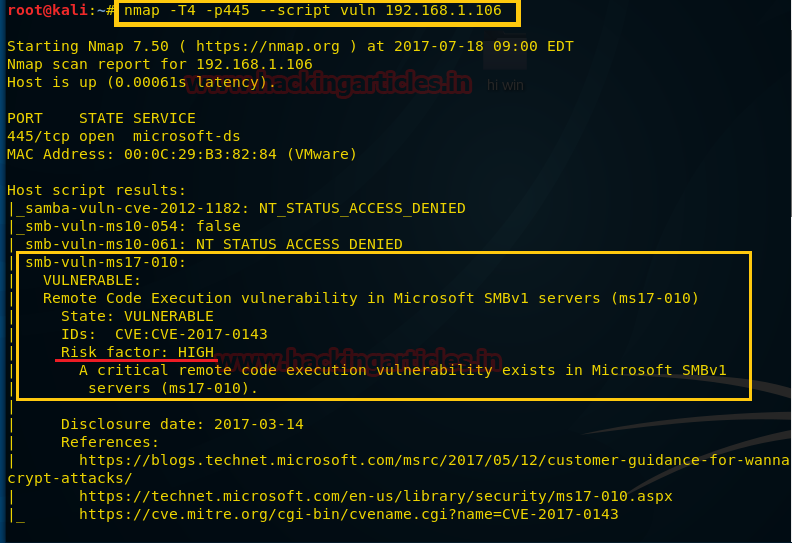
nmap -T4 -p445 --script vuln 192.168.1.106
You can observe from the given screenshot that port 445 is open and vulnerable. The target is exploitable to MS17-010 moreover Rate of Risk is High which mean it is easily vulnerable.
We can direct scan for SMB vulnerability for MS17-010 using NMAP script using following NMAP command:
nmap -T4 -p445 --script smb-vuln-ms17-010 192.168.1.106
From the given screenshot, you will observe that it has only scanned for MS17-010 and found the target is vulnerable against it.
From both results of NMAP, we have concluded that the target is vulnerable due to Microsoft SMBv1.

Metasploit
Uses information disclosure to determine if MS17-010 has been patched or not. Specifically, it connects to the IPC$ tree and attempts a transaction on FID 0. If the status returned is “STATUS_INSUFF_SERVER_RESOURCES”, the machine does not have the MS17-010 patch. If the machine is missing the MS17-010 patch, the module will check for an existing DoublePulsar (ring 0 shellcode/malware) infection. This module does not require valid SMB credentials in default server configurations. It can log on as the user “\” and connect to IPC$.
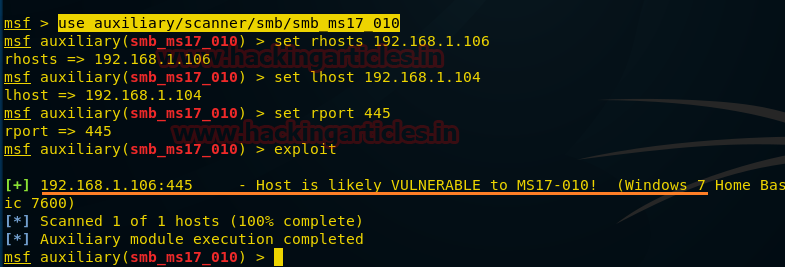
msf > use auxiliary/scanner/smb/smb_ms17_010 msf auxiliary(smb_ms17_010) > set rhosts 192.168.1.106 msf auxiliary(smb_ms17_010) > set lhost 192.168.1.104 msf auxiliary(smb_ms17_010) > set rport 445 msf auxiliary(smb_ms17_010) > exploit
From the screenshot, you can perceive that the host is vulnerable to MS17-010
Great!!! Now use MS17-010 to exploit your target.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Dear Sir,
I have found many IP are open on public and databases are having vulnerabilities.
Can you tell me how to inform to the user about it.